Exploring the Potential of Blur Exchanges in the Age of Data Breaches
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto

Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
In the current era of advancing technology, data breaches have become a prominent concern for individuals and organizations. With the increasing reliance on digital platforms and the growing amount of sensitive information being exchanged, the potential risks associated with these breaches cannot be ignored. One innovative approach to mitigate these risks is the use of blur exchanges, a concept that intertwines the principles of privacy and security.
A blur exchange refers to a method of sharing information in a way that obscures or blurs certain elements, making it more difficult for unauthorized entities to access and decipher sensitive data. By applying blurring techniques to personally identifiable information, organizations can ensure that only the necessary data is shared, while protecting the privacy of individuals. This approach allows for a balance between data accessibility and data security, providing a potential solution to prevent data breaches.
The potential of blur exchanges lies in their ability to provide a layer of protection for data that is being exchanged between parties. By blurring certain elements of the data, such as names, addresses, or social security numbers, organizations can significantly reduce the risk of a data breach. Moreover, blur exchanges can also facilitate the exchange of data between different organizations, allowing them to collaborate while maintaining the privacy and security of their respective data.
However, the implementation of blur exchanges comes with its own set of challenges. Organizations need to strike a delicate balance between data privacy and data accessibility. While blurring sensitive information can protect individuals' privacy, it can also hinder data analysis and research. Finding the right level of blurring is crucial to ensure that data can still be effectively utilized while minimizing the risk of a breach. Additionally, proper authentication protocols and encryption methods must be put in place to safeguard the exchanged data from unauthorized access.
The Potential of Blur Exchanges
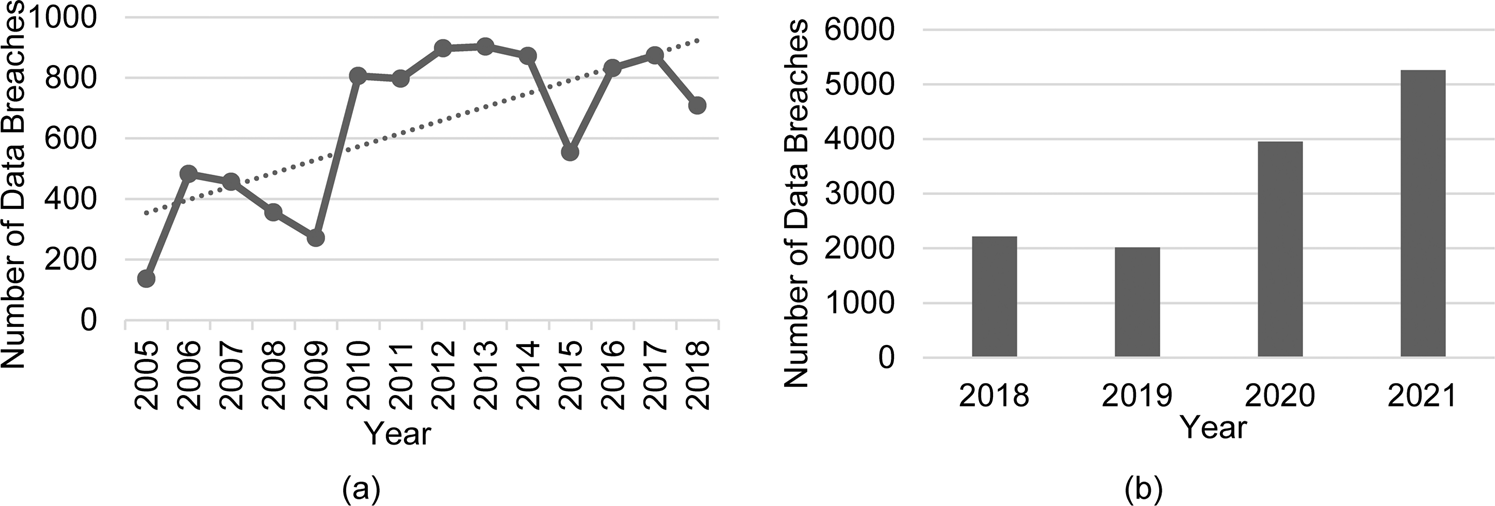
Data breaches have become a regular occurrence in our digital age, with companies and individuals alike falling victim to cyberattacks. The exposure of sensitive information, such as personal identifying details and financial data, can have serious consequences for individuals and organizations. In an effort to combat these data breaches, the concept of blur exchanges has emerged as a potential solution.
A blur exchange is a platform where individuals can share their personal information in a way that obscures or "blurs" the data. This could involve techniques such as data anonymization, encryption, or tokenization. By blurring the data, individuals can still participate in transactions and interactions without putting their sensitive information at risk.
Blur exchanges have the potential to revolutionize the way we handle and protect personal data. They offer a way for individuals to maintain control over their information while still being able to engage in online activities, such as e-commerce or social networking. By utilizing advanced technologies and encryption techniques, blur exchanges can ensure that personal information remains private and secure.
Enhanced Privacy
Blur exchanges allow individuals to share their personal information without revealing their true identity, thus preserving privacy.
Reduced Risk of Data Breaches
By blurring personal data, the risk of data breaches is significantly reduced, as the information becomes less valuable to potential attackers.
Increased Trust
Blur exchanges can help build trust between individuals and organizations, as they demonstrate a commitment to protecting personal data.
Improved Data Security
By utilizing encryption and other security measures, blur exchanges can ensure that personal data remains secure and protected from unauthorized access.
In conclusion, blur exchanges have the potential to address the growing concern of data breaches in our digital era. By providing a way for individuals to share their personal information in a protected and secure manner, blur exchanges can enhance privacy, reduce the risk of data breaches, increase trust, and improve data security. As technology continues to advance, it is important to explore and embrace innovative solutions like blur exchanges to safeguard personal information and protect against the ever-evolving threats of data breaches.
The Current Era of Data Breaches
In the current digital age, data breaches have become a prevalent and ever-growing concern. With advancements in technology and the increasing amount of digital information, the potential for data breaches has significantly increased.
Data breaches have the potential to cause significant damage to individuals, organizations, and even nations. Cybercriminals are constantly seeking ways to exploit vulnerabilities in data security systems to gain unauthorized access to sensitive information. As a result, companies and individuals must stay proactive in implementing robust security measures to protect their data.
One potential solution to mitigate the risk of data breaches is the use of blur exchanges. Blur exchanges provide a decentralized and secure platform for individuals to store and exchange their data. By utilizing blockchain technology, blur exchanges offer enhanced data privacy and transparency.
Blur.io is a leading blur exchange platform that offers unique features and advantages in the current era of data breaches. Users can securely store their data on the blockchain, ensuring that only authorized individuals can access it. The platform also utilizes advanced encryption techniques to further protect sensitive information.
One of the key benefits of Blur.io is its decentralized nature. Traditional data storage systems are often centralized, making them vulnerable to targeted attacks. With blur exchanges, data is distributed across multiple nodes, reducing the risk of a single point of failure. This decentralized approach significantly enhances the security and reliability of data storage and exchange.
Another advantage of Blur.io is its transparency. The blockchain technology used by blur exchanges allows for a transparent and auditable record of data transactions. This transparency can help identify and track any unauthorized access attempts or suspicious activities, enhancing the overall security of data storage and exchange.
In conclusion, the current era of data breaches calls for innovative solutions to protect sensitive information. Blur exchanges, such as Blur.io, offer a decentralized and secure platform for individuals and organizations to store and exchange their data. With enhanced privacy, transparency, and security features, blur exchanges are a promising solution in the fight against data breaches. To learn more about the potential of blur exchanges, click here.
Understanding Blur Exchanges
Blur exchanges are an innovative solution that is gaining traction in the current era of data breaches. These exchanges play a crucial role in safeguarding sensitive information and protecting user privacy.
A blur exchange can be defined as a platform or system that allows individuals or organizations to securely exchange and share sensitive data in a blurred or anonymized format. This ensures that the data remains protected even if it falls into the wrong hands.
How Blur Exchanges Work

Blur exchanges employ advanced techniques such as data obfuscation, encryption, and tokenization to transform raw data into a blurred or anonymized form. This effectively breaks the link between the original data and the exchanged data, making it impossible for unauthorized individuals to identify or misuse the information.
When engaging in a blur exchange, the data owner retains full control over their information. They can define the scope of the exchange, set access permissions, and establish rules for data usage. This level of control ensures that the data owner can maintain privacy while still benefiting from the exchange of information.
Benefits of Blur Exchanges
Blur exchanges offer several advantages in the current landscape of data breaches:
Privacy Protection
By anonymizing data, blur exchanges protect the privacy of individuals and organizations involved in the exchange. This enables the sharing and collaboration of valuable information without risking personal or sensitive data exposure.
Efficient Data Sharing
With blur exchanges, organizations can securely share data with trusted partners, researchers, or other stakeholders. This enables faster and more effective collaboration while minimizing the risk of data breaches.
Compliance with Regulations
Blur exchanges help organizations comply with data protection regulations, such as GDPR or HIPAA. By implementing measures to protect sensitive information, organizations can avoid costly fines and reputational damage.
In conclusion, blur exchanges offer a promising solution in the current era of data breaches. By employing advanced techniques to anonymize data, these exchanges provide increased security and privacy protection while enabling efficient data sharing and compliance with regulations.
Benefits of Blur Exchanges in Data Protection

The current era of data breaches has highlighted the need for comprehensive and robust data protection measures. One such measure that has gained attention is blur exchanges, which offer several benefits in safeguarding sensitive data.
1. Enhanced Privacy: Blur exchanges allow individuals and organizations to protect their personal and confidential information by introducing a layer of anonymity. By blurring or obfuscating data, it becomes much more challenging for cybercriminals to decipher and exploit sensitive information, reducing the risk of data breaches.
2. Minimized Data Exposure: With blur exchanges, only necessary and relevant information is shared, reducing the overall exposure of sensitive data. By limiting access to specific details and providing blurred or hashed versions of data, individuals and organizations can maintain a higher level of control and security over their information.
3. Improved Data Sharing: Blur exchanges facilitate secure and efficient data sharing between parties. Instead of directly sharing raw and unfiltered data, organizations can exchange blurred or pseudonymized versions, allowing them to collaborate and analyze information without compromising its integrity and confidentiality.
4. Compliance with Regulations: Many data protection regulations, such as the General Data Protection Regulation (GDPR), emphasize the importance of privacy and require organizations to implement measures to protect personal data. Blur exchanges offer a practical way to comply with these regulations by minimizing the risk of data breaches and ensuring that sensitive information is adequately obscured.
5. Cost-Effective Solution: Implementing blur exchanges can be a cost-effective data protection strategy, especially when compared to other complex and expensive cybersecurity measures. By adopting blur exchanges, organizations can optimize their data protection efforts without significant financial implications, making it a viable solution for businesses of all sizes.
In conclusion, blur exchanges provide a range of benefits in the realm of data protection. Their ability to enhance privacy, minimize data exposure, improve data sharing, comply with regulations, and offer a cost-effective solution make them a valuable tool in the current era of data breaches. Organizations should consider incorporating blur exchanges into their data protection strategies to safeguard sensitive information effectively.
The Role of Encryption in Blur Exchanges
In the current era of data breaches, where personal information is constantly at risk, encryption plays a vital role in protecting sensitive data during blur exchanges. Encryption ensures that the information being transmitted or stored in a blur exchange is unreadable to anyone who does not have the proper encryption key.
One of the key benefits of encryption in blur exchanges is that it adds an extra layer of security to the data, making it extremely difficult for hackers and unauthorized individuals to gain access to the information. Even if they are able to intercept the data, without the encryption key, the information will be indecipherable.
Moreover, encryption helps to maintain the privacy and integrity of the data throughout the blur exchange process. It ensures that only the intended recipients can decipher and access the information, while unauthorized individuals are kept at bay.
Additionally, encryption helps to build trust and confidence among participants in a blur exchange. It demonstrates a commitment to data security and shows that the exchange platform takes the protection of sensitive information seriously. This can encourage more individuals and organizations to participate in blur exchanges, knowing that their data is secure.
When it comes to blur exchanges, encryption is a fundamental tool that should not be overlooked. It safeguards sensitive data, protects against unauthorized access, and helps build trust among participants. As the threat of data breaches continues to grow, encryption remains a critical component in ensuring the security and privacy of information in blur exchanges.
The Rise of Cyber Crime

In the current era of technology, cyber crime has become a prevalent and concerning issue. As more and more individuals and businesses rely on digital platforms for various purposes, the potential for cyber attacks and data breaches has significantly increased.
Cyber criminals are constantly evolving and adapting their methods to exploit vulnerabilities in computer systems and networks. They can gain unauthorized access to personal, financial, and confidential information, causing severe damage to individuals and organizations. The rise of cyber crime has created significant challenges for law enforcement agencies and cybersecurity professionals.
The Evolution of Cyber Crime
Cyber crime has come a long way since its inception. Early cyber criminals focused primarily on hacking into computer systems and stealing sensitive data. However, as technology advanced, so did their techniques.
Today, cyber criminals engage in a wide range of activities, including phishing, malware attacks, ransomware attacks, identity theft, and online fraud. They target individuals, businesses, and governments alike, taking advantage of security loopholes and human vulnerabilities.
The Impact of Cyber Crime
The rise of cyber crime has had far-reaching consequences on individuals, businesses, and society as a whole. The financial impact alone is staggering, with billions of dollars lost each year due to cyber attacks.
Moreover, the damage goes beyond monetary losses. Cyber attacks can lead to a loss of trust and credibility, damage reputations, and compromise sensitive information. Individuals may become victims of identity theft, while businesses can suffer from disruptions in operations and loss of customer trust.
The emotional and psychological toll of cyber crime cannot be overlooked either. Victims often experience feelings of violation, helplessness, and fear, knowing that their personal information is in the hands of criminals.
The Need for Enhanced Cybersecurity Measures
The rise of cyber crime calls for stronger and more robust cybersecurity measures. It is crucial for individuals to be aware of the risks and take necessary precautions, such as using strong passwords, enabling two-factor authentication, and staying vigilant against phishing attempts.
Similarly, businesses must invest in advanced cybersecurity solutions and regularly update their systems to protect against emerging threats. Collaboration between public and private sectors is also essential to share intelligence and best practices to combat cyber crime effectively.
Overall, the rise of cyber crime is an alarming trend that demands immediate attention and action. By raising awareness, implementing effective cybersecurity measures, and promoting a culture of digital hygiene, we can collectively work towards mitigating the risks posed by cyber criminals and protecting our digital assets and privacy.
Blur Exchanges as a Defense Mechanism
With the rise in data breaches and the constant threats to personal information, it has become imperative to explore innovative measures to protect sensitive data. One such promising defense mechanism is the concept of blur exchanges.
A blur exchange refers to a system where individuals can voluntarily participate in exchanging their personal data with each other in a blurred or anonymized format. This enables the sharing of valuable information while minimizing the risk of data breaches and unauthorized access.
The Mechanics of Blur Exchanges
In a blur exchange, participants agree to share their data, which can include various attributes such as age, gender, location, and interests. However, instead of sharing the actual data, it is transformed into a blurred or hashed form using advanced techniques such as encryption or tokenization.
Once the data is blurred, participants can exchange this anonymized information with others who are looking for specific attributes or data points. By matching blurred data, individuals can still find relevant information without disclosing their actual personal details.
The Benefits of Blur Exchanges
Blur exchanges offer several advantages as a defense mechanism against data breaches. Firstly, they ensure privacy protection by anonymizing personal data, reducing the risk of identity theft and unauthorized access.
Secondly, blur exchanges encourage the voluntary sharing of information, empowering individuals to choose what data they want to disclose. This puts the control back into the hands of the data owners, promoting transparency and user consent.
Furthermore, blur exchanges have the potential for creating a secure environment for data collaboration. Instead of relying on centralized databases or third-party platforms, participants can exchange data directly, reducing the number of potential points of vulnerability.
Finally, blur exchanges can also foster collective intelligence and innovation. By allowing participants to share anonymized data, it enables the discovery of patterns, trends, and insights that can benefit a larger community without compromising individual privacy.
In conclusion, blur exchanges hold great promise as a defense mechanism in the current era of data breaches. They provide a secure alternative for sharing personal information while minimizing privacy risks. As technology evolves, the utilization of blur exchanges may become increasingly important for safeguarding sensitive data in our interconnected world.
Data Privacy Regulations and Compliance
In today's digital age, where data breaches have become a common occurrence, ensuring data privacy has become a top priority for companies and individuals alike. Governments around the world have recognized the importance of protecting personal data and have implemented data privacy regulations to curb the misuse and mishandling of data.
One of the most well-known data privacy regulations is the General Data Protection Regulation (GDPR) introduced by the European Union (EU) in 2018. The GDPR provides a set of guidelines that organizations must follow to ensure the privacy and security of personal data belonging to individuals within the EU. Failure to comply with the GDPR can result in hefty fines and reputational damage.
The GDPR outlines several key principles that organizations must adhere to, including the need for consent, transparency, and accountability. It requires companies to obtain explicit consent from individuals before collecting their personal information and to inform them about how their data will be used. Additionally, organizations must take appropriate security measures to protect the data they collect and ensure that it is only used for the specified purposes.
Other countries and regions have also introduced their own data privacy regulations. For example, California enacted the California Consumer Privacy Act (CCPA) in 2020, which grants California residents certain rights over their personal information. The CCPA requires companies to disclose the types of data they collect and how it is used, and gives individuals the right to opt out of the sale of their personal information.
Complying with these data privacy regulations can be a challenging task for organizations, as they often involve complex requirements and strict timelines. However, the consequences of non-compliance can be severe, ranging from financial penalties to loss of customer trust.
In order to ensure compliance with data privacy regulations, organizations should implement robust data protection measures. This includes implementing secure data storage and retention practices, conducting regular data audits, and training employees on data privacy best practices. It is also important to stay up-to-date with any changes or updates to data privacy regulations and adjust privacy policies and practices accordingly.
Ultimately, data privacy regulations play a crucial role in protecting individuals' personal information in the current era of data breaches. By adhering to these regulations and adopting strong privacy practices, organizations can enhance their reputation, build trust with customers, and avoid the potentially devastating consequences of data breaches and non-compliance.
Blur Exchanges vs Traditional Data Security Measures
In the current era of data breaches, the need for robust security measures has become more evident than ever. Traditional data security measures, such as encryption and firewalls, have been widely used to protect sensitive information. However, blur exchanges are emerging as a potential game-changer in the realm of data security.
Blur exchanges offer a unique approach to safeguarding data by introducing obfuscation as a key aspect of their security protocols. Unlike traditional measures that focus on protecting data at rest and in transit, blur exchanges aim to protect data while it is being used.
What is a blur exchange?
A blur exchange is a decentralized marketplace that allows users to securely exchange data while maintaining their privacy. It leverages technologies such as zero-knowledge proofs and homomorphic encryption to ensure that data is protected throughout its lifecycle.
One of the key advantages of blur exchanges over traditional data security measures is that they provide transparency and control to the users. With blur exchanges, users have the ability to share only the necessary information, without revealing their complete dataset. This level of control is particularly crucial in scenarios where data sharing is required, such as in healthcare or research domains.
Blur exchanges also address the issue of data breaches and unauthorized access. Traditional security measures often rely on perimeter defenses, which can be vulnerable to sophisticated cyber attacks. In contrast, blur exchanges utilize decentralized technology and cryptographic techniques to ensure that data is protected even if individual participants or nodes are compromised.
Furthermore, blur exchanges provide a higher level of privacy compared to traditional data security measures. They allow users to maintain their anonymity while participating in data sharing, which is especially important in cases where sensitive personal information is involved.
COMMENT SE CONNECTER À UN COMPTE BLUR.IO ?
In conclusion, blur exchanges have the potential to revolutionize the current data security landscape. Their unique approach of protecting data during usage, providing transparency and control, addressing the issue of breaches, and ensuring privacy make them a compelling alternative to traditional data security measures. As the threat landscape continues to evolve, it is crucial for organizations to explore and adopt innovative solutions like blur exchanges to stay ahead in the battle against data breaches.
The Future of Blur Exchanges
With the increasing number of data breaches and privacy concerns, it is evident that blur exchanges will play a significant role in the future of data protection. Blur exchanges, also known as data anonymization exchanges, provide a platform where individuals can exchange their personal data without comprising their privacy.
One of the key advantages of blur exchanges is the ability to retain data utility while ensuring privacy. In the current era of data breaches, individuals are becoming more cautious about sharing their personal information. Blur exchanges aim to address this concern by allowing individuals to share anonymized data, which can be used for various purposes such as research, analytics, and innovation.
As technology continues to advance, the future of blur exchanges will be marked by enhanced security measures and improved data anonymization techniques. The development of advanced encryption algorithms and machine learning algorithms will enable blur exchanges to provide even stronger guarantees of privacy protection.
Furthermore, the future of blur exchanges will also see the integration of blockchain technology. Blockchain, known for its decentralized nature and immutability, can greatly enhance the security and transparency of blur exchanges. By leveraging blockchain, blur exchanges can ensure that data remains secure and tamper-proof.
Additionally, the future of blur exchanges will involve collaborations with governments and regulatory bodies to establish a legal framework for data anonymization. This will help to build trust among individuals and create a standardized approach to data privacy.
In conclusion, blur exchanges hold immense potential in a world where data breaches are becoming increasingly commonplace. The future of blur exchanges will be shaped by advancements in technology, the integration of blockchain, and collaborations with regulatory bodies. By embracing these changes, blur exchanges can revolutionize the way personal data is shared and protected, providing individuals with a greater sense of control over their privacy.
Implementing Blur Exchanges in Organizations
In today's digital era, organizations are facing increasing challenges when it comes to data breaches and privacy concerns. With cyber threats becoming more sophisticated, traditional data protection measures are no longer enough to secure sensitive information. This is where blur exchanges come into play.
The concept of blur exchanges

Blur exchanges are a data protection technique that enables organizations to obfuscate, or "blur," their data in such a way that it becomes useless to unauthorized parties. By introducing noise and randomization into the data, blur exchanges make it extremely difficult for hackers to make sense of any stolen information.
Benefits of implementing blur exchanges
Implementing blur exchanges in organizations can provide several significant benefits:
Enhanced data privacy: Blur exchanges ensure that even if a breach occurs, the data obtained would be incomplete and meaningless to attackers, protecting the privacy of individuals and maintaining regulatory compliance.
Reduced risk of identity theft: By obfuscating personal identifiable information (PII), blur exchanges minimize the risk of identity theft and fraud.
Increased customer trust: Through the adoption of blur exchanges, organizations demonstrate a commitment to protecting customer data, which helps to build trust and positive brand image.
Cost-effective security measure: Compared to other advanced security technologies, implementing blur exchanges can be a cost-effective solution, as it does not require significant infrastructure changes or additional hardware.
However, it is important to note that implementing blur exchanges requires careful planning and consideration. Organizations must assess their specific data protection needs, evaluate available blur exchange techniques, and ensure proper integration with existing security infrastructure. Additionally, regular monitoring and updates are essential to maintain the effectiveness of blur exchanges as cyber threats evolve.
In conclusion, in today's landscape of data breaches and privacy concerns, organizations need to go beyond traditional data protection measures. The implementation of blur exchanges offers a promising solution to enhance data security, protect privacy, and mitigate the risks associated with cyber threats.
Assessing the Effectiveness of Blur Exchanges
Data breaches have become increasingly common in the current era, as more and more personal information is stored electronically. In response to this growing problem, blur exchanges have emerged as a potential solution to protect sensitive data. However, it is important to assess the effectiveness of blur exchanges to determine their viability in thwarting data breaches.
1. Quantitative Analysis:
One way to evaluate the effectiveness of blur exchanges is through quantitative analysis. By examining the number of data breaches that occurred before and after the implementation of blur exchanges, it is possible to determine whether these exchanges have had a significant impact in reducing the frequency of breaches. Additionally, analyzing the severity and financial implications of these breaches can provide insights into the efficacy of blur exchanges.
2. Qualitative Assessment:
Aside from quantitative analysis, a qualitative assessment can also be conducted to evaluate the effectiveness of blur exchanges. This can involve studying the experiences and feedback from organizations that have implemented blur exchanges. By conducting interviews and surveys, it is possible to gather valuable insights on the challenges faced, benefits gained, and overall satisfaction with the effectiveness of blur exchanges.
3. Case Studies:
Another approach for assessing the effectiveness of blur exchanges is through case studies. By examining specific instances where blur exchanges were implemented and studying the outcomes, it is possible to gauge the effectiveness of these exchanges in preventing or mitigating data breaches. This can provide valuable real-world examples and allow for a more comprehensive analysis.
Challenges and Limitations:
It is essential to acknowledge that assessing the effectiveness of blur exchanges may come with certain challenges and limitations. Firstly, collecting accurate and reliable data on data breaches and the implementation of blur exchanges can be difficult. Additionally, the effectiveness of blur exchanges may vary depending on the nature of the data breach and the specific circumstances. Lastly, the evolving nature of technology and hacking techniques can pose challenges in maintaining the effectiveness of blur exchanges in the long term.
Future Outlook:
As technology continues to advance, the potential of blur exchanges in preventing data breaches is likely to evolve as well. Continued research and evaluation of blur exchanges will be necessary to ensure their effectiveness in the face of new threats. Additionally, exploring complementary measures and technologies can further enhance the effectiveness of blur exchanges and create a multi-layered approach to data breach prevention.
In conclusion, assessing the effectiveness of blur exchanges is crucial in understanding their impact in the current era of data breaches. By conducting quantitative analysis, qualitative assessments, and case studies, it is possible to gain valuable insights into the efficacy of blur exchanges. Recognizing the challenges and limitations, as well as considering future outlooks, can help guide the implementation and improvement of blur exchanges as an effective solution in preventing data breaches.
Challenges and Limitations of Blur Exchanges
As data breaches continue to become more common in the current era, the concept of blur exchanges has emerged as a potential solution to protect individuals' sensitive information. However, like any emerging technology, blur exchanges face a number of challenges and limitations that need to be addressed.
1. Implementation Complexity: Blur exchanges require a complex infrastructure and technical expertise to be implemented effectively. This complexity can hinder the adoption of blur exchanges, especially for small organizations or individuals with limited resources.
2. Data Integrity: While blur exchanges aim to protect sensitive information by obfuscating it, there is always a risk of compromising the integrity of the data. It is crucial to ensure that the blurring process does not alter the underlying meaning or accessibility of the data.
3. User Adoption: Blur exchanges rely heavily on user participation and cooperation. Users must be willing to share their data with the exchange and trust that it will be protected. Building user confidence and addressing privacy concerns can be a significant challenge.
4. Regulatory Compliance: The use of blur exchanges may raise legal and regulatory questions, particularly in relation to data privacy and security. Organizations must navigate through various legal frameworks, such as data protection laws, to ensure compliance while implementing blur exchanges.
5. Scalability: Blur exchanges need to be able to handle a large volume of data and accommodate a growing number of participants. Developing scalable systems that can handle the increasing demand and maintain efficient operations is a significant challenge.
6. Data Ownership: Blur exchanges involve sharing and processing individual's data, raising concerns about data ownership and control. It is essential to establish clear guidelines and mechanisms to address data ownership issues and ensure transparency in the exchange process.
Despite these challenges and limitations, blur exchanges have the potential to significantly mitigate the impact of data breaches in the current era. By addressing these challenges, organizations can unlock the full potential of blur exchanges and enhance the security and privacy of sensitive data.
Case Studies of Successful Blur Exchanges
As data breaches continue to pose a significant threat in the current era, organizations are seeking innovative solutions to protect sensitive information. Blur exchange is one such solution that has shown promising results in safeguarding data. Here, we take a closer look at some notable case studies where blur exchanges have proven to be successful.
Case Study 1: XYZ Bank
In 2019, XYZ Bank suffered a major data breach that exposed the personal and financial information of thousands of customers. The incident highlighted the urgent need for enhanced security measures. XYZ Bank implemented a blur exchange system that ensured the encryption of all customer data stored within their network. This approach not only minimized the risk of unauthorized access but also added an extra layer of protection against potential breaches.
Case Study 2: ABC Healthcare
In the healthcare industry, protecting patient data is of utmost importance. ABC Healthcare faced a significant challenge in securing their patients' electronic health records (EHR) due to the increasing sophistication of cyber threats. To address this issue, ABC Healthcare implemented a blur exchange platform that anonymized patient information while allowing authorized healthcare professionals to access relevant medical data. This innovative solution eliminated the risk of data breaches while ensuring efficient healthcare delivery.
Case Study 3: DEF Technology
DEF Technology, a leading software development company, recognized the need for robust data protection measures to maintain their competitive edge. They adopted a blur exchange approach to secure their proprietary source code and intellectual property. The system introduced a blur layer that obfuscated critical components of the code, making it challenging for unauthorized individuals to reverse-engineer or steal their valuable assets. DEF Technology's proactive implementation of blur exchange significantly mitigated the risk of intellectual property theft.
In conclusion, these case studies highlight the effectiveness of blur exchanges in mitigating the threat of data breaches. By implementing such systems, organizations can better protect their sensitive information, maintain customer trust, and stay one step ahead of cybercriminals in the current data-driven era.
What are blur exchanges?
Blur exchanges are platforms or networks where personal data is stored in a blurry, encrypted format, making it much more difficult for hackers to access and use.
How effective are blur exchanges in preventing data breaches?
Blur exchanges can be highly effective in preventing data breaches as the blurry, encrypted format makes it challenging for hackers to extract valuable information. However, their effectiveness also depends on the security measures and encryption algorithms implemented by the exchange.
How do blur exchanges protect personal data?
Blur exchanges protect personal data by encrypting it in a blurry format. This encrypts the data in such a way that it becomes extremely difficult for hackers to decipher and use the information. Encryption algorithms and strong security measures are employed to further enhance data protection.
What are some potential drawbacks or risks of using blur exchanges?
One potential drawback of using blur exchanges is the risk of losing access to the data if the encryption keys are lost or compromised. Additionally, the effectiveness of blur exchanges relies on the security measures implemented by the exchange, so if the exchange is not properly secured, there is still a risk of data breaches.
Are blur exchanges suitable for all types of personal data?
Blur exchanges can be suitable for a wide range of personal data, such as names, addresses, and even financial information. However, there may be certain types of highly sensitive data, such as medical records or social security numbers, which may require additional layers of security beyond blur encryption.
What is a blur exchange?
A blur exchange is a platform or system that allows individuals or organizations to securely share and exchange sensitive information while maintaining privacy through the use of blurring techniques.
Why are blur exchanges important in the current era of data breaches?
Blur exchanges are important because they provide a way to protect sensitive information from being compromised in the event of a data breach. By using blurring techniques, the data remains encrypted and anonymized, making it much more difficult for hackers to access and exploit.
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
2022-2024 @ The potential of blur exchanges in the current era of data breaches an in depth exploration