Investigating the trustworthiness and security measures of the blur marketplace
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
Welcome to the fascinating world of the Blur Marketplace, where trust and security are paramount. In today's digital age, where online transactions have become the norm, it is crucial for any online marketplace to prioritize the safety and well-being of its users. The Blur Marketplace recognizes this, and has implemented a series of trust and security protocols to ensure a seamless and secure experience for its users.
One of the key features that sets the Blur Marketplace apart is its robust user verification system. Before users can start buying or selling on the platform, they must go through a thorough verification process. This process includes providing identification documents, such as a passport or driver's license, and verifying their payment methods. By implementing this stringent verification process, the Blur Marketplace ensures that only genuine and trustworthy users are allowed on the platform.
To further enhance trust among its users, the Blur Marketplace has also implemented a sophisticated rating and review system. After each transaction, both buyers and sellers have the opportunity to rate and leave feedback for their counterpart. This allows users to make informed decisions based on the experiences of others, ensuring a transparent and reliable marketplace. The rating and review system also incentivizes users to provide high-quality products and services, as their reputation is at stake.
In addition to user verification and the rating system, the Blur Marketplace employs cutting-edge encryption and security measures to safeguard user data and financial transactions. By utilizing industry-standard encryption protocols, such as SSL/TLS, the platform ensures that all communication and data transfers are protected against unauthorized access. Furthermore, the Blur Marketplace regularly conducts security audits and implements proactive measures to identify and mitigate potential vulnerabilities, giving users peace of mind when conducting transactions on the platform.
In conclusion, the trust and security protocols implemented by the Blur Marketplace set it apart as a reliable and secure online marketplace. Through robust user verification, a comprehensive rating and review system, and state-of-the-art encryption technology, the Blur Marketplace provides users with a trustworthy platform for buying and selling. So, whether you are a buyer or a seller, you can explore the Blur Marketplace with confidence, knowing that your safety and security are of utmost importance.
Importance of trust and security in an online marketplace

Trust and security are vital factors in any online marketplace, including the blur marketplace. With the increasing popularity of e-commerce, it has become crucial to establish a safe and trustworthy environment for both buyers and sellers.
1. Protection against fraud: Trust and security protocols play a pivotal role in preventing fraud and ensuring the integrity of transactions. By implementing authentication measures, such as user verification and secure payment gateways, the blur marketplace can safeguard its users' personal and financial information.
2. Building customer confidence: Trust is fundamental to building a strong customer base. When buyers feel secure and confident in an online marketplace, they are more likely to engage in transactions. The implementation of trust indicators, such as customer reviews, seller ratings, and dispute resolution mechanisms, can positively influence customer confidence and loyalty.
3. Protecting sensitive information: Online marketplaces deal with sensitive information such as credit card details, addresses, and personal data. Robust security protocols, including encryption and secure communication channels, are essential to protect this information from unauthorized access and cyberattacks.
4. Preventing counterfeit products: Trust and security protocols help mitigate the risk of counterfeit products being sold on the platform. By implementing procedures for verifying sellers and ensuring the quality and authenticity of products, the blur marketplace can maintain a reliable reputation and protect its users from fraud.
5. Promoting fairness and accountability: Trust and security protocols promote fairness and accountability among all marketplace participants. By creating clear guidelines, enforcing policies, and providing transparent communication channels, the blur marketplace can foster a sense of trust and ensure that all users are treated fairly.
6. Protecting against identity theft: In an online marketplace, users often share personal information that could potentially be exploited by identity thieves. Implementing security measures, such as two-factor authentication and regular security audits, can significantly reduce the risk of identity theft and protect the privacy of users.
7. Encouraging user engagement: By prioritizing trust and security, the blur marketplace can encourage user engagement and drive more transactions. When users know that their interests are protected and that they can expect a safe and reliable experience, they are more likely to actively participate in the marketplace and recommend it to others.
In conclusion, trust and security are essential pillars of any online marketplace. By establishing robust protocols and implementing measures to protect users' information and interests, the blur marketplace can create a trustworthy and secure environment that fosters user confidence, promotes fair transactions, and ensures the long-term success of the platform.
Trust Protocols
When it comes to the Blur marketplace, trust is a vital aspect of the platform. Users need to have confidence that their transactions will be secure and that they can trust the sellers they are dealing with. This is why the Blur marketplace has implemented a range of trust protocols to ensure the safety and security of all users.
One of the main trust protocols implemented by the Blur marketplace is a thorough verification process for sellers. Before a seller can list any items for sale, they must go through a rigorous verification process, which includes providing personal information and proof of ownership of the assets they are selling. This helps to ensure that sellers are genuine and can be trusted by buyers.
Additionally, the Blur marketplace has implemented an escrow system to offer an extra layer of protection for buyers. When a buyer purchases an item, the payment is held in escrow until the item is delivered. This ensures that the buyer's funds are secure and gives them peace of mind that they will receive the item they paid for.
To further enhance trust on the platform, the Blur marketplace also utilizes a reputation system. This system allows users to rate and review sellers based on their experiences. This feedback is visible to other users and helps to create a transparent and trust-based community. Buyers can also make informed decisions based on the reputation of sellers, promoting a safer marketplace environment.
In conclusion, the trust protocols implemented by the Blur marketplace are aimed at creating a secure and trustworthy environment for all users. Through seller verification, an escrow system, and a reputation system, users can have confidence in their transactions and know that they are dealing with trustworthy sellers. To learn more about Blur Crypto, you can visit their official website at What Is Blur Crypto.
User verification process
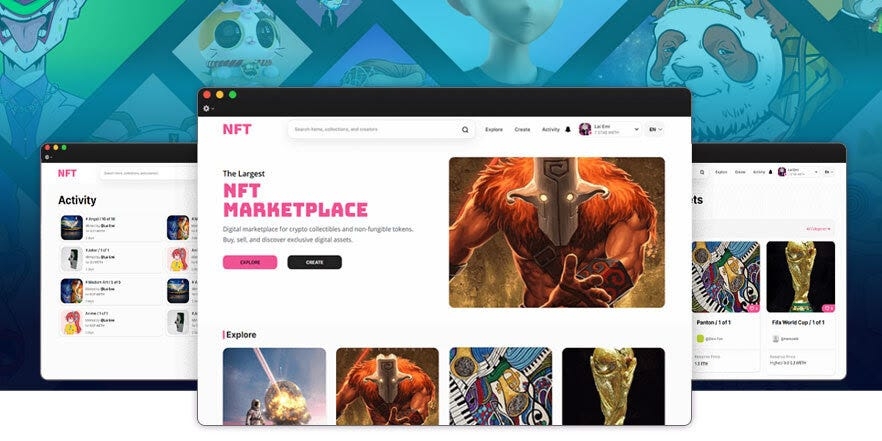
The blur marketplace has implemented a rigorous user verification process to ensure the trust and security of its platform. This process involves several steps to ensure that all users are genuine and can be trusted.
Email Verification: When a user signs up for an account on the blur marketplace, they are required to verify their email address. This is done by sending a verification link to the provided email address. Users must click on this link to confirm their email and activate their account.
Phone Number Verification: After the email verification, users are prompted to verify their phone number. They are sent a verification code via SMS, which they need to enter on the platform to complete the verification process. This step ensures that users provide a valid phone number and helps prevent the creation of multiple fake accounts.
Identity Verification: In order to increase trust on the platform, the blur marketplace also offers identity verification for users who wish to have a verified account. This involves submitting a government-issued ID, such as a passport or driver's license, along with a recent photo. The marketplace verifies the identity of the user by comparing the information provided with the submitted documents.
By implementing these verification steps, the blur marketplace aims to create a safe and secure environment for its users. The process ensures that users are who they claim to be and can be trusted when engaging in transactions on the platform.
Reputation System
In the blur marketplace, the reputation system plays a crucial role in establishing trust and ensuring secure transactions between buyers and sellers. This system allows users to build and maintain their reputation through successful transactions and positive feedback from other users.
When users interact on the blur marketplace, they have the ability to rate their experience and provide feedback on the quality of the products or services they received. This feedback is then used to calculate a user's reputation score, which is displayed on their profile.
The reputation score is a numerical value that represents a user's overall trustworthiness and reliability within the blur marketplace. A higher reputation score indicates a user who has a history of successful transactions and positive feedback, making them more trustworthy in the eyes of other users.
Having a reputation system in place helps users make informed decisions when engaging with other users on the blur marketplace. Before entering into a transaction, users can view the reputation scores of potential buyers or sellers, giving them an idea of the reliability and trustworthiness of the person they are dealing with.
In addition to the reputation score, the blur marketplace also provides a detailed feedback system. Users can leave comments alongside their rating, providing more specific information about their experience with a particular buyer or seller. This feedback can be instrumental in helping other users assess the reputation of a user before engaging in a transaction.
The reputation system fosters a sense of accountability among users on the blur marketplace. It incentivizes users to provide exceptional service and maintain a positive reputation, as a low reputation score or negative feedback can hinder their ability to attract potential buyers or sellers.
The blur marketplace understands the importance of trust and security in facilitating successful transactions. By implementing a robust reputation system, the marketplace aims to promote a safe and reliable environment for users to buy and sell goods and services.
For more information on the trust and security protocols implemented by the blur marketplace, please visit: Connecting to Blur.io: Exploring the Features and Advantages of Blur.io.
Dispute Resolution Mechanism

The Blur marketplace has established a comprehensive and efficient dispute resolution mechanism to ensure trust and security among its participants. This mechanism is designed to handle any disagreements or conflicts that may arise during transactions, providing a fair and unbiased resolution process for both buyers and sellers.
When a dispute occurs, the first step is for the involved parties to communicate and attempt to reach a resolution on their own. They are encouraged to engage in open dialogue and negotiate a mutually acceptable solution. If they are unable to reach an agreement, they can escalate the dispute to the Blur marketplace's support team.
The support team will then step in to mediate the dispute and facilitate communication between the parties. They will carefully review all relevant information, including transaction records, communication logs, and any additional evidence provided by both parties. This impartial analysis helps the support team gain a thorough understanding of the dispute and make an informed decision.
The resolution process aims to consider all aspects of the transaction and evaluate the validity of each party's claims. The support team will assess the adherence to the marketplace's terms and conditions, as well as any applicable laws or regulations. They will strive to reach a fair and equitable resolution that upholds the principles of trust, transparency, and accountability.
Once the support team reaches a decision, they will communicate it to both parties involved in the dispute. The decision will be binding and must be respected by both parties. The resolution process is designed to help maintain a safe and secure marketplace environment, as well as protect the rights and interests of all participants.
It is important to note that the dispute resolution mechanism is intended for genuine disputes and conflicts. Any attempts to abuse or exploit the system may result in penalties, including account suspension or termination. The Blur marketplace encourages all participants to engage in honest and transparent transactions, promoting a trustworthy and reliable online marketplace for all users.
Security Protocols
The blur marketplace has implemented a range of security protocols to ensure the safety and trustworthiness of the platform. These protocols are designed to protect both buyers and sellers from potential threats and fraudulent activities.
Password Protection
One of the fundamental security measures is the implementation of password protection. Each user is required to create a strong, unique password that is difficult to guess or crack. The platform enforces password complexity requirements, such as a minimum length and a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, the platform uses secure hashing algorithms to store passwords, ensuring that even if the database is compromised, the original passwords cannot be easily obtained.
Secure Communication

The blur marketplace utilizes secure communication protocols, such as SSL/TLS, to encrypt data transmitted between users and the platform. Encryption ensures that sensitive information, such as login credentials and payment details, cannot be intercepted or deciphered by malicious actors. This helps to protect the confidentiality and integrity of users' personal information.
Furthermore, the platform incorporates mechanisms to verify the authenticity and integrity of communications. Digital signatures and certificates are used to confirm the identity of users and ensure that messages have not been tampered with during transmission.
In addition to encrypting user communication, the platform also employs secure channels for financial transactions. Payment information is transmitted via established and reputable payment gateways, which comply with industry standards and best practices for securing online transactions.
Secure Transaction Escrow
To provide an extra layer of security for buyers and sellers, the blur marketplace utilizes a secure transaction escrow system. This system holds funds in a secure account until the buyer receives and approves the purchased goods or services. This helps to prevent scams and disputes by ensuring that the seller does not receive payment until the buyer confirms satisfaction with the transaction.
The escrow service also assists in resolving any disputes that may arise between the parties involved. In the event of a disagreement, the platform provides mediation and arbitration services to facilitate a fair resolution that benefits all parties.
Overall, the blur marketplace prioritizes the security and trust of its users by implementing various protocols and measures to safeguard their information and transactions. These security protocols work together to create a safe and reliable environment for buyers and sellers to engage in transactions with confidence.
Encryption and Data Protection
In order to ensure the trust and security of the blur marketplace, robust encryption and data protection protocols have been implemented. These measures are designed to safeguard user information and prevent unauthorized access to sensitive data.
Data Encryption
All user data, including personal and financial information, is encrypted using industry-standard encryption algorithms. This ensures that even if an unauthorized party gains access to the data, it will be unreadable and unusable without the decryption key.
The encryption process converts plain text data into ciphertext, which can only be decrypted back into its original form with the correct encryption key. This ensures that user data remains confidential and inaccessible to unauthorized individuals.
Secure Communication
In addition to data encryption, secure communication protocols are implemented to protect information during transmission. HTTPS, or HTTP Secure, is employed to encrypt data transferred between the user's device and the blur marketplace servers.
This ensures that sensitive information, such as login credentials and transaction details, are protected from interception and eavesdropping. HTTPS uses SSL/TLS protocols to establish an encrypted connection, providing a secure and private means of communication.
Physical and Network Security
The blur marketplace's physical infrastructure is protected with state-of-the-art security measures to prevent unauthorized access to servers and equipment. Access controls, surveillance systems, and firewalls are deployed to safeguard against physical and network-based attacks.
Redundant backup systems and disaster recovery plans are also in place to ensure the continuity and availability of user data. Regular security audits and vulnerability assessments are conducted to identify and address potential security risks.
Industry-standard encryption algorithms
Secure communication protocols (HTTPS)
Physical and network security measures
Regular security audits and vulnerability assessments
Secure payment options
In order to ensure a secure and trustworthy transaction environment, the Blur Marketplace offers a variety of secure payment options for its users. These payment options have been carefully selected and implemented to prioritize the privacy and security of both buyers and sellers.
Payment Escrow: To prevent fraudulent transactions, Blur Marketplace utilizes a payment escrow system. When a buyer makes a purchase, the payment amount is held in escrow until the transaction is successfully completed. This ensures that the seller only receives payment once the buyer has confirmed that the product or service has been delivered as expected.
Secure Payment Gateways: The marketplace integrates with reputable, secure payment gateways to process transactions. These payment gateways use advanced encryption and security measures to protect sensitive financial information, such as credit card details or bank account information, ensuring that the buyer's payment information is secure.
Cryptocurrency Payments: With the growing popularity of cryptocurrencies, Blur Marketplace supports secure cryptocurrency payments. This option provides an extra layer of privacy and security, as cryptocurrency transactions are decentralized and encrypted. It allows buyers and sellers to transact without revealing personal information, reducing the risk of identity theft or fraud.
Two-Factor Authentication (2FA): To further enhance account security, Blur Marketplace offers two-factor authentication. This adds an extra layer of protection by requiring users to enter a unique code generated by a trusted authentication app in addition to their login credentials. This ensures that even if a user's password is compromised, unauthorized access to their account is prevented.
By offering these secure payment options, the Blur Marketplace aims to provide a safe and trustworthy platform for buyers and sellers. These measures help to protect users' financial information, prevent fraudulent transactions, and foster a secure environment for conducting business.
Two-factor authentication
Two-factor authentication (2FA) is a security measure implemented by the blur marketplace to provide an additional layer of protection for user accounts. It adds an extra step to the login process, requiring users to provide two different forms of identification: something they know (such as a password) and something they have (such as a verification code).
The blur marketplace utilizes a time-based one-time password (TOTP) for the second factor of authentication. When users enable 2FA on their accounts, they are required to download a trusted authenticator app, such as Google Authenticator or Authy, to generate the verification codes.
Once 2FA is enabled, when users log in to their accounts, they are prompted to enter their passwords as the first factor. Then, they are asked to provide the verification code generated by the authenticator app as the second factor. This adds an additional layer of security as it ensures that even if an attacker manages to obtain a user's password, they would still require access to the user's authentication device to log in.
Enabling two-factor authentication is highly recommended for all users of the blur marketplace. It significantly reduces the risk of unauthorized access to user accounts and provides users with peace of mind knowing that their accounts are well-protected.
Trust and Security Audits
Trust and security are crucial aspects of any online marketplace, and Blur Marketplace recognizes the importance of establishing a safe and secure environment for its users. To ensure the trustworthiness of its platform, Blur Marketplace regularly conducts trust and security audits.
Third-Party Audits

Blur Marketplace engages third-party security firms and experts to conduct comprehensive audits of its trust and security protocols. These audits are aimed at identifying vulnerabilities, assessing the strength of existing security measures, and recommending improvements. Third-party audits provide an unbiased evaluation of the platform's security practices and help enhance its overall level of trust.
Continuous Monitoring
Trust and security audits are not a one-time event for Blur Marketplace. They are part of an ongoing process of continuous monitoring and improvement. The marketplace employs various monitoring tools and techniques to detect any potential security threats or breaches proactively.
Regular scanning and penetration testing are conducted to identify and address any vulnerabilities in the system. This proactive approach helps ensure the platform remains secure and trustworthy for all its users.
Encryption and Data Protection
Blur Marketplace understands the importance of protecting user data and employs robust encryption protocols to safeguard sensitive information. All user data, including personal details and financial transactions, are encrypted during transmission and storage.
Moreover, Blur Marketplace follows industry best practices to comply with relevant data protection regulations, ensuring that user information is handled securely and in compliance with applicable privacy laws.
In conclusion, trust and security audits play a crucial role in maintaining the integrity and reliability of the Blur Marketplace. By engaging in regular audits and continuous monitoring, the marketplace demonstrates its commitment to providing a safe and secure online platform for its users.
Regular third-party audits
One of the key measures implemented by the blur marketplace to ensure trust and security is regular third-party audits. These audits are performed by reputable and independent organizations to assess the marketplace's security protocols, data protection measures, and compliance with industry standards and regulations.
By conducting regular audits, the blur marketplace demonstrates its commitment to transparency and accountability. It allows for an objective evaluation of the marketplace's security posture and helps identify any potential vulnerabilities or weaknesses that need to be addressed.
During these audits, the third-party organization thoroughly examines the marketplace's infrastructure, systems, and processes. They assess the effectiveness of the implemented security controls, such as encryption, access controls, and authentication mechanisms, to ensure they are functioning as intended and effectively protect user data.
In addition to technical assessments, the audits also evaluate the marketplace's adherence to privacy regulations and best practices. This includes reviewing the marketplace's data handling procedures, consent management, and user rights management to ensure compliance with applicable privacy laws.
The findings of these audits are carefully reviewed by the blur marketplace's security team, who work towards remedying any identified issues or weaknesses. This iterative process ensures that the marketplace stays up-to-date with the evolving threat landscape and continuously improves its security and privacy practices.
By undergoing regular third-party audits, the blur marketplace provides users with assurance that their data is handled securely and in accordance with industry best practices. It demonstrates the marketplace's proactive approach towards protecting user trust and maintaining a secure environment for transactions.
In conclusion, regular third-party audits play a critical role in establishing and maintaining trust in the blur marketplace. By subjecting its security practices and protocols to independent scrutiny, the marketplace can ensure the highest levels of trust and security for its users.
Penetration Testing
Penetration testing, also known as ethical hacking, plays a crucial role in evaluating the security and trust protocols implemented by the Blur marketplace. This testing method involves a systematic attempt to exploit vulnerabilities in a system and uncover potential weaknesses that could be exploited by malicious actors.
Penetration testing is conducted by trained professionals who simulate real-world attack scenarios to identify and prioritize vulnerabilities. These professionals use a combination of manual and automated techniques to identify weak points in the system, such as insecure network configurations, software vulnerabilities, and weak user access controls.
Benefits of Penetration Testing

Penetration testing provides numerous benefits for the Blur marketplace, including:
Identification of Vulnerabilities: Penetration testing helps identify vulnerabilities in the system's design, implementation, and configuration, ensuring they can be addressed before they are exploited by attackers.
Confirmation of Security Measures: By conducting penetration testing, the Blur marketplace can validate the effectiveness of its security measures and protocols, ensuring they meet industry standards and best practices.
Improved Incident Response: By uncovering vulnerabilities and weaknesses, penetration testing allows the Blur marketplace to strengthen its incident response capabilities and develop strategies to mitigate the impact of potential breaches.
Compliance Requirements: Penetration testing helps the Blur marketplace meet compliance requirements, such as those outlined by regulatory bodies or industry standards like PCI DSS.
Penetration Testing Process
The penetration testing process typically involves the following steps:
Planning and Preparation: In this phase, goals, scope, and rules of engagement are determined. This includes identifying the systems to be tested, the testing methods to be used, and the potential impact on the production environment.
Reconnaissance: During this phase, information gathering techniques are used to gather intelligence about the target systems, including IP addresses, open ports, and potential vulnerabilities.
Vulnerability Assessment: In this phase, vulnerabilities and weaknesses in the target systems are identified using automated tools and manual analysis.
Exploitation: In this phase, the identified vulnerabilities are exploited by the penetration testers to gain unauthorized access or extract sensitive information.
Escalation: This phase involves escalating privileges or moving laterally within the target systems to uncover additional vulnerabilities.
Reporting: Finally, the penetration testers document their findings, including identified vulnerabilities, exploitation methods, and recommendations for remediation.
To ensure the effectiveness of the penetration testing process, it is essential for the Blur marketplace to engage experienced and reputable penetration testing professionals. Regular penetration testing should also be conducted to adapt to evolving security risks and address new vulnerabilities as they arise.
Identification of Vulnerabilities
Planning and Preparation
Confirmation of Security Measures
Reconnaissance
Improved Incident Response
Vulnerability Assessment
Compliance Requirements
Exploitation
Escalation
Reporting
Bug Bounty Program
The Blur Marketplace takes security seriously and has implemented a Bug Bounty Program to encourage external researchers to help identify and report any security vulnerabilities or bugs on the platform. This program allows security experts to actively participate in improving the platform's security by finding and reporting potential issues.
How does the Bug Bounty Program work?
Anyone can participate in the Bug Bounty Program by identifying and reporting security vulnerabilities or bugs found on the Blur Marketplace. To participate, follow these steps:
Visit the Blur Marketplace website and create an account WIE MAN SICH BEI BLUR.IO ANMELDET.
Thoroughly test the platform and its security protocols.
If you find any vulnerabilities or bugs, document them with detailed steps to reproduce the issue.
Submit your findings through the Bug Bounty Program's dedicated reporting channel using the provided submission form.
Once your report is received, the Blur Marketplace team will review and validate the findings.
If your findings are valid, you may be eligible for a bug bounty reward, which will be determined based on the severity and impact of the reported vulnerability or bug.
Program Guidelines and Rules
To ensure a fair and efficient Bug Bounty Program, the Blur Marketplace has established the following guidelines and rules:
Do not attempt any harmful or malicious activities on the platform or its users.
Do not publicly disclose any vulnerabilities or bugs before they have been resolved and validated by the Blur Marketplace team.
Do not disrupt or impair the normal functioning of the platform while testing.
Do respect user privacy and data integrity during your testing process.
The Blur Marketplace appreciates the efforts of security researchers and values the importance of their contributions to the overall security of the platform. By participating in the Bug Bounty Program, you will not only help improve the security of the Blur Marketplace but also earn recognition and potentially receive a monetary reward for your findings.
Customer Support

Customer support plays a vital role in building trust and ensuring the security of the Blur Marketplace. Our dedicated customer support team is available 24/7 to assist users with any issues or concerns they may have.
When it comes to trust and security, we understand the importance of promptly addressing any incidents or questions. Our knowledgeable customer support representatives are trained to handle a variety of situations, ranging from account security to transaction disputes.
We employ various communication channels to provide convenient customer support. Users can reach out to us via email, phone, or our online chat feature. Additionally, we have an extensive FAQ section on our website that answers common questions and provides useful information regarding account security and transaction safety.
When interacting with our customer support team, users can expect an empathetic and understanding approach. We prioritize listening to our users' concerns and work diligently to resolve any issues in a timely manner.
In addition to our customer support team, we have implemented comprehensive security protocols to protect user information and transactions. This includes using encryption technology to safeguard sensitive data and implementing firewalls to prevent unauthorized access.
At Blur Marketplace, we believe that trust and security are the foundation of a successful online marketplace. Our commitment to providing reliable customer support and implementing robust security protocols sets us apart from other platforms.
If you have any questions or need assistance, please don't hesitate to contact our customer support team. We are here to ensure your experience on the Blur Marketplace is secure and enjoyable.
How secure is the blur marketplace?
The blur marketplace has implemented multiple trust and security protocols to ensure the security of user data and transactions. These include encryption, two-factor authentication, and regular security audits.
What measures are taken to protect user data on the blur marketplace?
The blur marketplace has a strong focus on protecting user data. All user data is encrypted using industry-standard encryption algorithms. Additionally, user data is stored on secure servers and access to this data is strictly controlled and monitored.
Can I trust the blur marketplace with my financial information?
Yes, you can trust the blur marketplace with your financial information. The marketplace has implemented robust security measures to protect your financial data. These measures include encryption, two-factor authentication, and regular security audits.
How does the blur marketplace ensure the security of transactions?
The blur marketplace ensures the security of transactions through various protocols. These protocols include encryption of sensitive information, two-factor authentication for account access, and regular security audits to identify and address any vulnerabilities.
What steps does the blur marketplace take to prevent fraud?
The blur marketplace takes several steps to prevent fraud. These steps include monitoring user activity for suspicious behavior, implementing strict verification processes for sellers, and providing dispute resolution mechanisms to protect buyers and sellers.
What are the trust and security protocols implemented by the blur marketplace?
The trust and security protocols implemented by the blur marketplace include encryption of user data, two-factor authentication for account access, and a comprehensive review system for service providers.
How does the blur marketplace ensure the security of user data?
The blur marketplace ensures the security of user data through encryption, which protects the information from unauthorized access. This means that even if a breach occurs, the data would be incomprehensible to anyone without the decryption key.
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
2022-2024 @ Exploring the trust and security protocols implemented by the blur marketplace