Key information for users to understand the potential dangers of the blur.io platform
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto

Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
Blur io platform has gained significant popularity among users looking to connect and interact with others online. The platform allows users to communicate through text, images, and video, making it a versatile and accessible option for social interaction. However, it is crucial for users to be aware of the potential dangers that can arise while using this platform.
First and foremost, it is important to remember that not everyone on blur io platform may have good intentions. Users should exercise caution when sharing personal information, such as their full name, address, or contact details. There have been instances of individuals using these platforms to gather personal information and potentially engage in fraudulent activities.
Additionally, users should be mindful of the potential for cyberbullying and harassment on blur io platform. While the platform provides a means for connecting with others, it also opens the door for negative interactions. It is essential for users to take steps to protect themselves and report any instances of harassment or bullying that they may encounter.
Furthermore, it is important to be wary of scams and phishing attempts on blur io platform. Users should be cautious when engaging with unknown individuals or clicking on suspicious links or attachments. Criminals may attempt to deceive users with fake profiles or messages in order to gain access to personal information or infect devices with malware. It is advisable to verify the authenticity of any requests or messages before taking any action.
Ultimately, while blur io platform offers numerous benefits and opportunities for connection, it is crucial for users to remain vigilant and cautious. By being aware of the potential dangers and taking necessary precautions, users can have a safer and more enjoyable online experience.
Identifying the risks of using the blur io platform
When using the blur io platform, it is important for users to be aware of the potential risks involved. While the platform offers various benefits and opportunities, it also presents certain dangers that users should consider. This article aims to highlight some of the key risks associated with using the blur io platform.
1. Security Risks
One of the primary concerns when using any online platform is the security of personal information and funds. The blur io platform, like any other online marketplace, is not immune to security breaches and cyber attacks. Users should be cautious and take necessary measures to protect their accounts, such as setting strong passwords, enabling two-factor authentication, and regularly monitoring their transactions.
Additionally, users should be wary of phishing attempts and scams that may target blur io platform users. It is important to verify the authenticity of any communication or request before sharing personal or financial information.
2. Counterfeit and Illegitimate Listings
The blur io platform allows users to buy and sell various digital assets, including NFTs (Non-Fungible Tokens). However, there is a risk of encountering counterfeit or illegitimate listings on the platform. Despite the platform's efforts to enforce guidelines and policies, it is possible for fraudulent or unauthorized items to be listed by dishonest users.
Users should be vigilant and do their due diligence before making any purchases on the blur io platform. It is advisable to research the authenticity and history of sellers, verify the legitimacy of listed items, and check for any red flags or suspicious activities.
3. Market Volatility
Another risk to consider when using the blur io platform is market volatility. The value of digital assets, including NFTs, can be highly unpredictable and subject to rapid fluctuations. Users should be prepared for the possibility of potential financial losses if the market takes a downturn.
It is important for users to carefully evaluate and assess the risks associated with any investments or purchases made on the blur io platform. Users should be aware that the value of digital assets can be influenced by various factors, including market trends, demand, and external events.
In conclusion, while the blur io platform offers exciting opportunities and benefits for users, it also carries certain risks that should not be overlooked. By understanding and being aware of these risks, users can take necessary precautions to protect themselves and make informed decisions when using the platform.
For more information about blur io platform and its benefits, please visit What Is Blur Crypto.
Ensuring Privacy and Data Security on blur io Platform
Privacy and data security are top concerns for users of the blur io platform. With the ever-increasing amount of personal information being shared online, it is crucial to take necessary measures to protect your data from unauthorized access and potential misuse.
1. Strong User Authentication
blur io takes user authentication seriously to ensure that only authorized individuals have access to the platform. Users are required to create strong and unique passwords that are not easily guessable. Two-factor authentication (2FA) is also available as an additional layer of security, requiring users to provide a verification code in addition to their password.
2. Encryption of Data
All communication between the user's device and the blur io platform is encrypted using industry-standard encryption protocols. This ensures that any data transferred between the user and the platform cannot be intercepted or tampered with by unauthorized parties.
3. Secure Storage of Data

The user's data is stored securely on the blur io platform. Data is encrypted at rest, meaning that even if an unauthorized person gains access to the storage system, they will not be able to access or understand the encrypted data.
4. Limited Data Sharing

blur io takes the privacy of its users seriously and does not share user data with third parties without explicit consent. Any sharing of data is done in accordance with applicable data protection laws and regulations.
5. Regular Security Audits
blur io conducts regular security audits to identify and address any potential vulnerabilities in the platform. This helps ensure that the platform remains secure and up-to-date with the latest security practices.
By following these measures, blur io strives to provide its users with a secure and private platform for communication and collaboration. However, users also have a responsibility to take necessary precautions, such as not sharing sensitive information with unknown or untrusted parties, to ensure their own privacy and data security.
Protecting personal information when using blur io platform

When using the blur io platform, it is important to take steps to protect your personal information and ensure your online safety. Here are some essential tips:
Create a strong and unique password: Choose a password that is not easy to guess and is not used for any other accounts. Use a combination of uppercase and lowercase letters, numbers, and symbols.
Enable two-factor authentication: This adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, when logging in.
Be cautious with sharing personal information: Avoid sharing sensitive information, such as your full name, address, or financial details, in public chat rooms or with unknown individuals.
Secure your device: Keep your operating system, antivirus software, and other applications up to date to protect against security vulnerabilities. Install a reliable firewall and use a reputable VPN service when accessing the blur io platform.
Be aware of phishing attempts: Stay vigilant for suspicious emails or messages that ask for personal information or contain malicious links. Avoid clicking on unknown links and never share your login credentials via email or other insecure channels.
Use a separate email address: Consider using a separate email address for registering on the blur io platform and avoid using your primary email for website sign-ups to minimize the risk of potential data breaches.
Review privacy settings: Regularly review and update your privacy settings on the blur io platform to ensure that only necessary information is shared and visible to others.
Stay informed about platform updates: Keep an eye on any security updates and guidelines provided by the blur io platform. This will help you stay up to date with the latest security measures and protect your personal information.
By following these precautions, you can better protect your personal information and enjoy a safer experience when using the blur io platform.
Recognizing the Possibility of Cyberattacks on the blur io Platform
As an user of the Blur: NFT login platform, it's important to be aware of the potential risks and dangers associated with cyberattacks. While the blur io platform strives to provide a safe and secure online environment, it's crucial for users to understand the threats that exist in order to protect themselves and their valuable information.
Cyberattacks can take various forms, including but not limited to:
1. Phishing: These attacks involve deceptive emails, messages, or websites that mimic legitimate platforms or institutions. Cybercriminals often use social engineering techniques to trick users into providing sensitive information such as passwords, credit card details, or personal identification information.
2. Malware: Malicious software can be disguised as innocuous files or downloads, including email attachments or software installations. Once installed, malware can gain unauthorized access to a user's personal data, track their online activities, or even control their device remotely.
3. Brute Force Attacks: In a brute force attack, cybercriminals repeatedly attempt to guess a user's password or encryption key by systematically trying all possible combinations. This method can be time-consuming but poses a serious threat if a user's password is weak or easily guessable.
4. SQL Injection: This type of attack targets web applications that interact with databases. Cybercriminals exploit vulnerabilities in the application's code to manipulate or extract sensitive information from the database, potentially gaining access to user accounts, personal data, or financial information.
5. Man-in-the-Middle: In this attack, a cybercriminal intercepts the communication between a user and a service or platform. By positioning themselves between the two parties, they can eavesdrop on sensitive information such as login credentials, financial transactions, or personal messages.
In order to protect yourself from these potential cyberattacks on the blur io platform, it's important to take the following precautions:
1. Use Strong Passwords: Choose complex passwords that include a combination of letters, numbers, and special characters. Avoid using easily guessable information such as birth dates or common phrases.
2. Enable Two-Factor Authentication (2FA): Utilize the additional layer of security provided by 2FA, which requires both a password and a unique verification code to access your account.
3. Keep Software Updated: Regularly update your operating system, web browser, and antivirus software to ensure you have the latest security patches and protections against known vulnerabilities.
4. Be Mindful of Suspicious Emails and Links: Exercise caution when clicking on links or opening attachments from unknown or suspicious sources. Phishing attacks often rely on unsuspecting users to unknowingly provide access to their personal information.
By understanding the potential dangers and taking appropriate precautions, users can minimize the risk of falling victim to cyberattacks on the blur io platform. Stay informed, stay vigilant, and protect your online presence.
Preventing scams and fraudulent activities on blur io platform
As with any online platform, it is important to be aware of the potential risks of scams and fraudulent activities on blur io. While the platform takes measures to ensure the safety of its users, it is crucial for users to stay vigilant and take steps to protect themselves as well.
1. Verified profiles
One of the ways to reduce the risk of scams is to only interact with verified profiles on blur io. The platform has a verification process in place to confirm the identity of its users. When engaging with other users, look for the verification badge on their profile to ensure they are legitimate.
2. Secure transactions
When conducting transactions on blur io, it is important to prioritize security. Avoid sharing personal or financial information, such as credit card details or social security numbers, in public chats or messages. Use the platform's built-in payment system for transactions to ensure a secure and traceable process.
3. Research and read reviews

Before engaging in any business or transaction on blur io, it is wise to do some research and read reviews about the user you are dealing with. Look for any negative feedback or reports of fraudulent activities. Trust your instincts and be cautious when dealing with users who have a limited presence or suspicious history.
4. Avoid upfront payments
Avoid making upfront payments or sending money to other users on blur io without proper verification and assurance. Scammers often ask for upfront payments and then disappear without delivering the promised goods or services. Be wary of any requests for payment outside of the secure payment system provided by blur io.
5. Report suspicious activities
If you come across any suspicious activities or suspect someone of being involved in scams on blur io, report it to the platform's support team immediately. Provide as much information as possible, including usernames, chat conversations, and any evidence of fraudulent behavior. Reporting scams helps protect other users from falling victim to fraudulent activities.
By following these precautions and being cautious when interacting with other users, you can minimize the risk of scams and fraudulent activities on the blur io platform. Remember, your safety and security should always be a top priority when using any online platform.
Avoiding potential pitfalls of sharing sensitive information on blur io platform
The blur io platform offers a convenient and user-friendly way to share information and collaborate with others. However, it is important to be cautious when sharing sensitive information on the platform to protect your privacy and security. Here are some potential pitfalls to avoid:
1. Check privacy settings

Before sharing any sensitive information on blur io, carefully review the privacy settings for your account and the specific files or documents you plan to share. Make sure you understand who can access, view, and download your files. Adjust the settings accordingly to ensure that only trusted individuals or authorized parties have access.
2. Use encryption for sensitive files
If you need to share highly sensitive files on blur io, consider encrypting them before uploading. Encryption adds an extra layer of security by scrambling the data, making it unreadable without the correct decryption key. There are various encryption software programs and tools available that you can utilize to protect your sensitive files.
Additionally, you should avoid sharing sensitive information, such as passwords or financial data, directly on blur io. Instead, use secure communication channels for sharing this type of information, such as encrypted emails or secure messaging apps.
3. Be cautious about the recipients

Before sharing sensitive information, ensure that you are sharing it with the intended recipients only. Double-check the email addresses or usernames to avoid accidentally sending it to the wrong person. Take extra precautions when sharing sensitive information with individuals you do not know well or trust.
4. Regularly review and manage shared files

It is important to regularly review and manage the files you have shared on blur io. Remove any files that are no longer necessary or relevant to minimize the risk of unauthorized access. Keep track of the files you have shared and ensure they are securely stored or deleted when they are no longer needed.
Unauthorized access to shared files
Check privacy settings and limit access to trusted individuals
Data breaches and security vulnerabilities
Use encryption for sensitive files and avoid sharing passwords or financial data directly on blur io
Accidental sharing with wrong recipients
Double-check recipients' information before sharing sensitive files
Retention of unnecessary shared files
Regularly review and manage shared files, deleting them when no longer needed
By following these tips and being mindful of the potential pitfalls, you can safely share sensitive information on the blur io platform and protect your privacy and security.
Being aware of the risks of online harassment through blur io platform
As with any online platform, there are potential risks and dangers that users should be aware of when using blur io. One of these risks is online harassment, which can occur when individuals use the platform as a means to bully, intimidate, or threaten others.
Online harassment on blur io can take many forms, including but not limited to:
Verbal abuse: Users may engage in derogatory language, insults, or offensive comments towards others.
Cyberbullying: This involves intentionally targeting and harassing individuals with the intent to cause emotional distress.
Doxxing: Some users may attempt to disclose and share private information about others, which can have severe consequences.
Stalking: Certain individuals may use the blur io platform to monitor, follow, or track the activities of others without their consent.
Threats and intimidation: Users may employ the platform to convey threats or intimidate others, creating a hostile environment.
It is crucial for users of blur io to understand the potential risks associated with online harassment and take necessary precautions to protect themselves. Here are a few tips to stay safe while using the platform:
Set your privacy settings: Ensure that your personal information is only visible to trusted users and limit access to your profile.
Block and report: If you encounter any instances of online harassment, utilize the platform's reporting and blocking features to protect yourself.
Keep evidence: If you are a victim of online harassment, save any offensive messages or interactions as evidence, which may be useful if further action is required.
Reach out for support: If you feel unsafe or threatened, consider confiding in a trusted friend, family member, or seek support from relevant authorities.
Practice digital literacy: Enhance your knowledge about online safety, privacy, and security to recognize and avoid potential risks.
Remember, online harassment is a serious issue that can have detrimental effects on individuals' mental health and overall well-being. By being aware of the risks and taking proactive measures to mitigate them, users can enjoy a safer and more positive experience on blur io.
Understanding the Consequences of Engaging with Suspicious Users on Blur io Platform
The Blur io platform is an emerging marketplace for NFTs, offering users the opportunity to buy, sell, and trade unique digital assets. While the platform provides a convenient and exciting way to engage with the NFT community, it is important for users to be aware of the potential dangers associated with interacting with suspicious users.
1. Phishing and Scams
One of the major consequences of engaging with suspicious users on the Blur io platform is the risk of falling victim to phishing attacks and scams. These users may reach out to you with enticing offers or requests for personal information, aiming to deceive you and gain unauthorized access to your account or funds.
To protect yourself, always be cautious when sharing personal information or engaging in financial transactions with unknown users. Be wary of any requests for sensitive information and never click on suspicious links or provide your credentials to unauthorized sources.
2. Unauthorized Access

Engaging with suspicious users on Blur io can also lead to unauthorized access to your account or digital assets. These users may attempt to gain control over your NFTs, steal your login credentials, or deploy malware that can compromise your device.
To mitigate the risk of unauthorized access, it is crucial to enable strong security measures such as two-factor authentication (2FA) and regularly update your login credentials. Additionally, refrain from clicking on suspicious links or downloading files from unknown sources to prevent malware infections.
3. Financial Loss
Another consequence of interacting with suspicious users is the potential for financial loss. These users may engage in fraudulent transactions, scamming you out of your money or valuable NFTs. Once the transaction is completed, it can be difficult to recover the lost funds.
To minimize the risk of financial loss, it is recommended to only engage in transactions with reputable and verified users on the platform. Always do your due diligence, research the user's reputation, and use escrow services or smart contracts to ensure a secure transaction process.
By understanding the consequences of engaging with suspicious users on the Blur io platform, users can better protect themselves and their digital assets. Remember to stay vigilant, follow best cybersecurity practices, and report any suspicious activity to the platform administrators. For more information, visit the Blur: NFT login website.
Managing online reputation and avoiding reputational damage on blur io platform
As a user of the blur io platform, it is important to understand the significance of managing your online reputation to avoid any potential reputational damage. In today's digital world, where information spreads quickly and is easily accessible, it is crucial to maintain a positive online image.
Why online reputation management is important
Your online reputation can greatly impact how others perceive you, both personally and professionally. Potential employers, business partners, and even friends and family may form opinions based on what they find about you online. Therefore, it is essential to actively manage your online presence to shape a positive reputation.
Blur io platform is no exception to the online reputation game. The platform allows users to interact, share content, and engage with others. Anything you post or participate in can be seen and evaluated by others. It is important to remember that even seemingly harmless actions can have consequences.
Tips for managing your online reputation on blur io platform
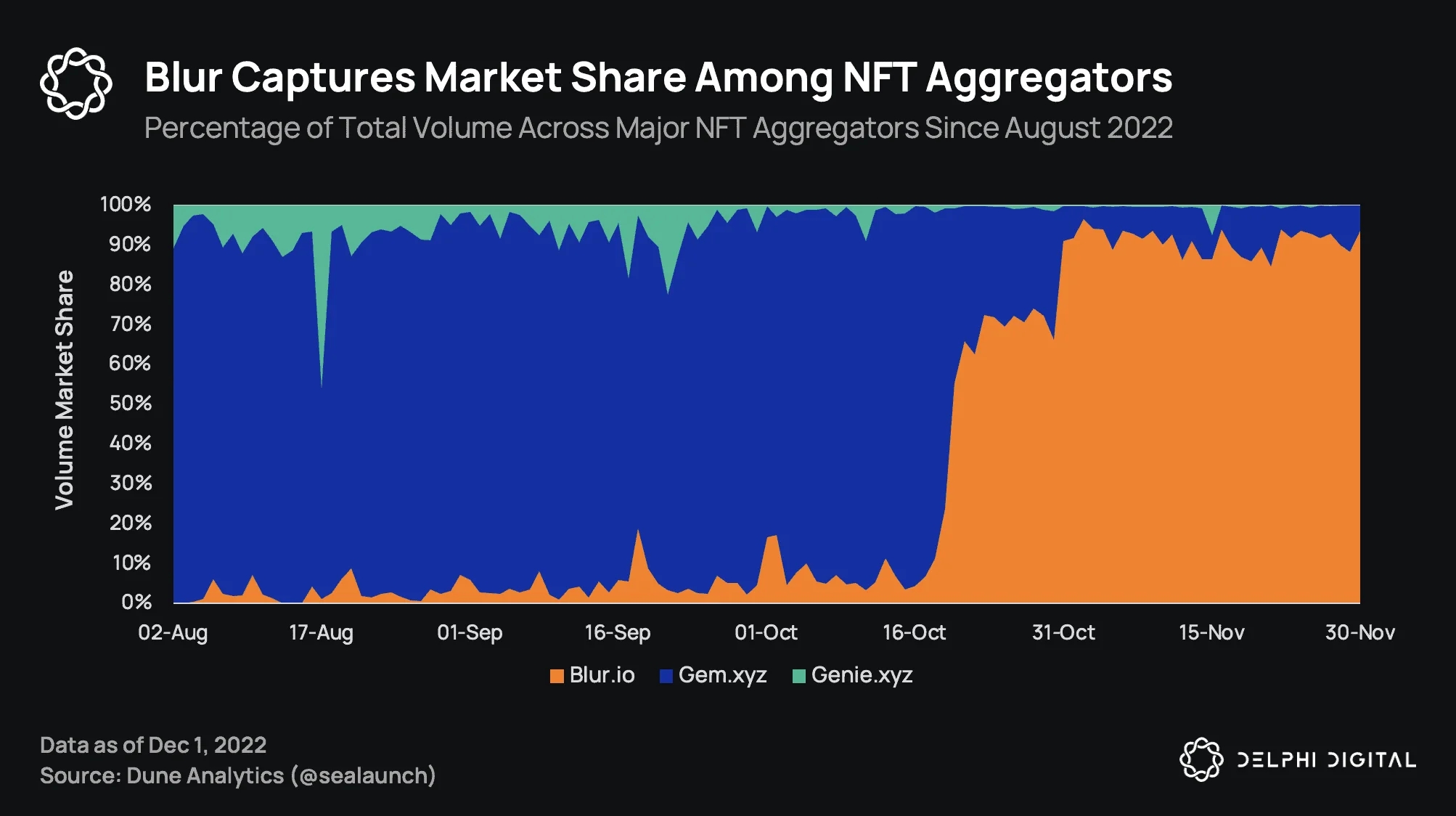
1. Be mindful of what you share: Before posting anything on blur io, think about how it may be perceived by others. Avoid sharing discriminatory or offensive content, as it can lead to significant reputational damage. What you post reflects your values and beliefs, so choose your words and content wisely.
2. Practice responsible commenting: Engage in respectful and constructive discussions on blur io platform. Avoid engaging in online debates that may escalate into hostile arguments. Be aware of the impact your comments can have on your reputation and always be respectful towards others.
3. Regularly monitor your online presence: Keep an eye on what others are saying about you on the platform. Search your name on blur io to see if there are any negative or questionable posts or comments related to you. If you find any, address them promptly and professionally.
4. Engage with positive content: Actively participate in positive discussions, content sharing, and collaborations on blur io platform. By engaging with high-quality and valuable content, you can contribute positively to your online reputation.
Remember, your online reputation is not only about what you post, but also how you interact with others and respond to situations on the blur io platform. Practice good online etiquette and be aware of the potential consequences of your actions to maintain a positive image.
Staying Updated on the Latest Security Measures of the blur io Platform
As a user of the blur io platform, it is crucial to stay informed about the latest security measures implemented to protect your data and ensure a safe browsing experience. By keeping up to date with the platform's security features, you can enhance your online privacy and reduce the risk of potential dangers.
Here are some key ways to stay updated on the latest security measures of the blur io platform:
Frequently check for platform updates: Blur io regularly releases updates to address security vulnerabilities and improve its overall security infrastructure. Make sure to check for updates frequently and install them promptly to benefit from the latest security enhancements.
Subscribe to the blur io blog: The blur io blog is an excellent resource for staying informed about the platform's latest security measures and feature updates. By subscribing to the blog, you will receive notifications whenever new security-related content or updates are published.
Follow blur io on social media: Blur io maintains active social media accounts, including Twitter, Facebook, and LinkedIn. Following these accounts will provide you with regular updates on security measures, data breaches, and tips for maintaining online privacy.
Enable two-factor authentication (2FA): Two-factor authentication adds an extra layer of security to your blur io account. By enabling 2FA, you will receive a unique verification code on your registered mobile device, which you'll need to enter along with your password to access your account. This additional step adds a significant barrier to potential unauthorized access.
Review privacy policy and terms of service: Familiarize yourself with blur io's privacy policy and terms of service regularly. These documents outline the platform's data handling practices, security measures, and user obligations. Staying updated on these policies will help you understand how your information is being protected.
Participate in security awareness training: Blur io provides security awareness training sessions for its users. These sessions cover various topics such as identifying phishing attempts, secure browsing practices, and password management. Participating in these training sessions will help you develop a stronger understanding of potential security risks and avoid falling victim to them.
Report any suspicious activities or vulnerabilities: If you come across any suspicious activities or identify potential vulnerabilities on the blur io platform, report them immediately to the platform's security team. By doing so, you contribute to the ongoing efforts to keep the platform secure for all users.
Remember, security is a shared responsibility between the platform provider and the users. By staying informed and actively participating in the security measures, you can help create a safer environment for yourself and other blur io platform users.
Reporting and addressing any security concerns on blur io platform
If you come across any security issues or suspicious activities on the blur io platform, it is essential to report them immediately to ensure a safe and secure environment for all users. The blur io team takes security seriously and encourages users to actively participate in maintaining a secure platform.
Identifying security concerns:
There are several indicators that can help you identify potential security concerns on the blur io platform. These include:
Unusual or suspicious behavior: If you notice any unusual or suspicious behavior, such as strange messages, requests for personal information, or activities that seem deceptive, it is important to report them.
Phishing attempts: Be vigilant of any messages or links that appear to be phishing attempts, aiming to deceive users into revealing sensitive information. Do not click on suspicious links or provide personal information in response to such messages.
Unauthorized access: If you suspect unauthorized access to your account or someone else's account, report it immediately. This could include instances where your account credentials have been stolen or if you notice any unfamiliar activities.
Reporting security concerns:
When reporting security concerns on the blur io platform, follow these steps:
Contact blur io support: Reach out to the blur io support team via their official email or customer support channels. Provide detailed information about the security concern, including any relevant messages, usernames, or timestamps.
Monitor your account: While waiting for a response from the blur io team, monitor your account for any additional suspicious activities. Change your password and enable extra security measures, such as two-factor authentication, if available.
Cooperate with the blur io team: If the blur io team requests additional information or assistance in investigating the security concern, cooperate fully to ensure timely resolution and prevent any further security risks.
Addressing security concerns:
The blur io team takes prompt action to address reported security concerns. Depending on the severity and nature of the issue, their actions may include:
Investigation: The blur io team will thoroughly investigate the reported security concern to determine its validity and potential impact.
Resolution: Once the issue is confirmed, the blur io team will take the necessary steps to fix the security vulnerability, prevent any further harm, and secure the platform.
User notifications: If a security concern has affected multiple users, the blur io team may send out notifications or alerts to inform and guide users on how to protect themselves.
Preventive measures: To prevent similar security concerns in the future, the blur io team may enhance their security systems, update their policies, or provide additional security awareness resources to users.
Remember, staying vigilant and promptly reporting any security concerns is crucial for maintaining a safe environment on the blur io platform. The contribution of each user in identifying and addressing security risks is highly valued and helps ensure a secure and enjoyable experience for all.
What is the blur io platform?
The blur io platform is an online gaming platform that allows users to play various multiplayer games.
Are there any potential dangers associated with using the blur io platform?
Yes, there are potential dangers associated with using the blur io platform. Users should be aware of the risks of online gaming, such as cyberbullying, exposure to inappropriate content, and potential addiction.
How can users protect themselves from potential dangers on the blur io platform?
Users can protect themselves from potential dangers on the blur io platform by being cautious about sharing personal information, using strong and unique passwords, reporting any inappropriate behavior or content, and setting boundaries on their gaming time.
What should parents do to ensure their children's safety on the blur io platform?
Parents should monitor their children's online activity, set rules and guidelines for gaming, educate their children about online safety, and have open and honest conversations about the potential dangers of the blur io platform.
Is it possible to have a safe and enjoyable gaming experience on the blur io platform?
Yes, it is possible to have a safe and enjoyable gaming experience on the blur io platform by taking necessary precautions, being mindful of one's online behavior, and utilizing the available safety features and parental controls.
What is the blur io platform?
The blur io platform is a popular online gaming platform where users can play multiplayer games. It allows players from all over the world to connect and compete against each other in various games.
What are some potential dangers of using the blur io platform?
There are several potential dangers of using the blur io platform. One of the main risks is encountering cyberbullying or harassment from other players. Another danger is the possibility of downloading malware or viruses from unofficial sources. Additionally, users should be cautious about sharing personal information on the platform, as it can be accessed by other players.
How can users protect themselves from the potential dangers of the blur io platform?
Users can protect themselves by following a few precautions while using the blur io platform. They should avoid sharing personal information, such as their full name, address, or phone number, with other players. It is also important to report any instances of cyberbullying or inappropriate behavior to the platform's administrators. Additionally, users should only download games and content from official sources to avoid the risk of malware or viruses.
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
2022-2024 @ Understanding the potential dangers of blur io platform essential information for users