Why encryption is crucial for maintaining security on the blur io platform
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto

Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
In today's digital age, ensuring the security and privacy of user data is of utmost importance. As more and more interactions take place online, the need for robust encryption mechanisms becomes critical. One platform that recognizes this need is blur io, a cutting-edge technology that prioritizes the protection of user information. By employing advanced encryption techniques, blur io ensures that user data remains secure and inaccessible to unauthorized individuals.
Encryption is the process of encoding information in a way that it can only be decoded by authorized parties, thus ensuring the confidentiality and integrity of the data. With the rise in cyber threats, encryption plays a vital role in safeguarding sensitive information from being intercepted or tampered with. This is particularly crucial for platforms like blur io that handle vast amounts of user data, including personal details, financial information, and communication records.
One of the main advantages of encryption on the blur io platform is that it provides end-to-end security. This means that the data is encrypted before it leaves the sender's device, and it remains encrypted until it reaches the intended recipient. This strong encryption protocol ensures that even if the data is intercepted during transit, it remains unreadable and unusable to unauthorized entities. By implementing end-to-end encryption, blur io creates a secure environment for users to share and store their information.
Furthermore, encryption also helps protect user data from potential breaches and unauthorized access within the blur io system itself. With encryption in place, even if an attacker manages to gain access to the platform's servers, they would be unable to make sense of the encrypted data without the appropriate decryption keys. This adds an additional layer of security and significantly reduces the risk of data compromise.
In summary, encryption is a fundamental component in maintaining the security and privacy of user data on the blur io platform. By employing advanced encryption techniques, blur io ensures that user information remains confidential and protected from cyber threats. With end-to-end encryption and robust security measures, blur io sets the standard for secure communication and data storage in the digital age.
The Power of Encryption in Ensuring Security on the blur io Platform
Encryption plays a vital role in maintaining the security and privacy of users on the blur io platform. By utilizing encryption techniques, blur.io is able to safeguard sensitive data and prevent unauthorized access.
One of the key benefits of encryption is the ability to protect user information from being intercepted or accessed by unauthorized parties. Through the use of encryption algorithms, such as AES (Advanced Encryption Standard), data transmitted between users and the blur io server is converted into an unreadable format. This ensures that even if an attacker intercepts the data, they would not be able to decipher its contents without the encryption key.
Another important aspect of encryption is data integrity. Encryption algorithms not only encrypt the data but also generate a unique signature, or a digital fingerprint, for each encrypted piece of information. This signature is used to verify the integrity of the data during transmission and storage. If any tampering or modifications occur, the signature will not match, indicating a breach in data integrity.
Furthermore, encryption helps prevent data leaks and unauthorized access to user accounts. By encrypting user passwords, blur io ensures that even in the event of a security breach, the passwords are stored in an encrypted format. This adds an additional layer of protection, as the stored passwords cannot be easily decrypted and used by an attacker.
Additionally, encryption is crucial for securing sensitive user information, such as credit card details or personal identification numbers. By encrypting this data, blur io ensures that even if the information is accessed by an unauthorized individual, it remains protected and unusable.
Overall, encryption is a powerful tool in ensuring the security and privacy of users on the blur io platform. By implementing robust encryption techniques, such as AES, blur io can provide users with a secure environment for their data and transactions, promoting trust and confidence in the platform.
Understanding the Significance of Encryption
In today's digital age, where data is constantly being transmitted and stored, the significance of encryption cannot be overstated. Encryption plays a critical role in maintaining security and ensuring the integrity of information on the blur io platform. By converting data into an unreadable format, encryption provides a safeguard against unauthorized access, interception, and tampering.
Protection of Sensitive Data
Encryption acts as a protective barrier for sensitive data, such as personal information, financial details, and confidential business records. Without encryption, this data would be vulnerable to cybercriminals and unauthorized individuals who may attempt to exploit it for personal gain or malicious purposes. By encrypting data, it becomes virtually impossible for anyone to make sense of the information without the corresponding decryption key, even if they manage to gain access to it.
Secure Communication
Encryption is essential for secure communication on the blur io platform. When users exchange messages or share files, encryption ensures that the information remains private and confidential. By encrypting the data at the sender's end and decrypting it at the recipient's end, the risk of interception or eavesdropping is significantly reduced. Encrypted communication channels offer users peace of mind, knowing that their messages and files are protected from prying eyes.
Moreover, encryption also prevents the alteration and manipulation of data during transmission. By using encryption, the blur io platform guarantees the authenticity and integrity of the information being exchanged between users.
Compliance with Privacy Regulations

Encryption is not only crucial for security reasons but also for complying with privacy regulations. In many jurisdictions, organizations are legally required to protect sensitive information, such as personally identifiable information (PII), by implementing encryption measures. Failure to comply with these regulations can result in severe penalties and reputational damage. By incorporating encryption into the blur io platform, it ensures that users' data is handled in accordance with relevant privacy laws and regulations.
Encryption mitigates the risk of data breaches and unauthorized access.
Encrypted data remains secure even if the device or storage medium is lost or stolen.
Encryption fosters trust between users and the blur io platform, encouraging greater adoption.
Properly implemented encryption algorithms are robust against cryptographic attacks.
In conclusion, encryption plays a vital role in maintaining security on the blur io platform. It not only protects sensitive data, ensures secure communication, and complies with privacy regulations but also fosters trust and confidence among users. By embracing encryption as an integral part of the platform's security architecture, blur io can enhance its reputation as a trusted and secure platform for users to exchange information.
Maintaining Confidentiality with Encryption
In the digital age, maintaining the confidentiality of sensitive information is crucial. Without proper measures, unauthorized individuals can gain access to personal data, financial details, and other sensitive information, leading to devastating consequences. Encryption plays a vital role in safeguarding this information from unauthorized access by converting it into a code that can only be deciphered by authorized parties.
Se connecter à Blur.io : Explorer les caractéristiques et les avantages de Blur.io
How Encryption Works
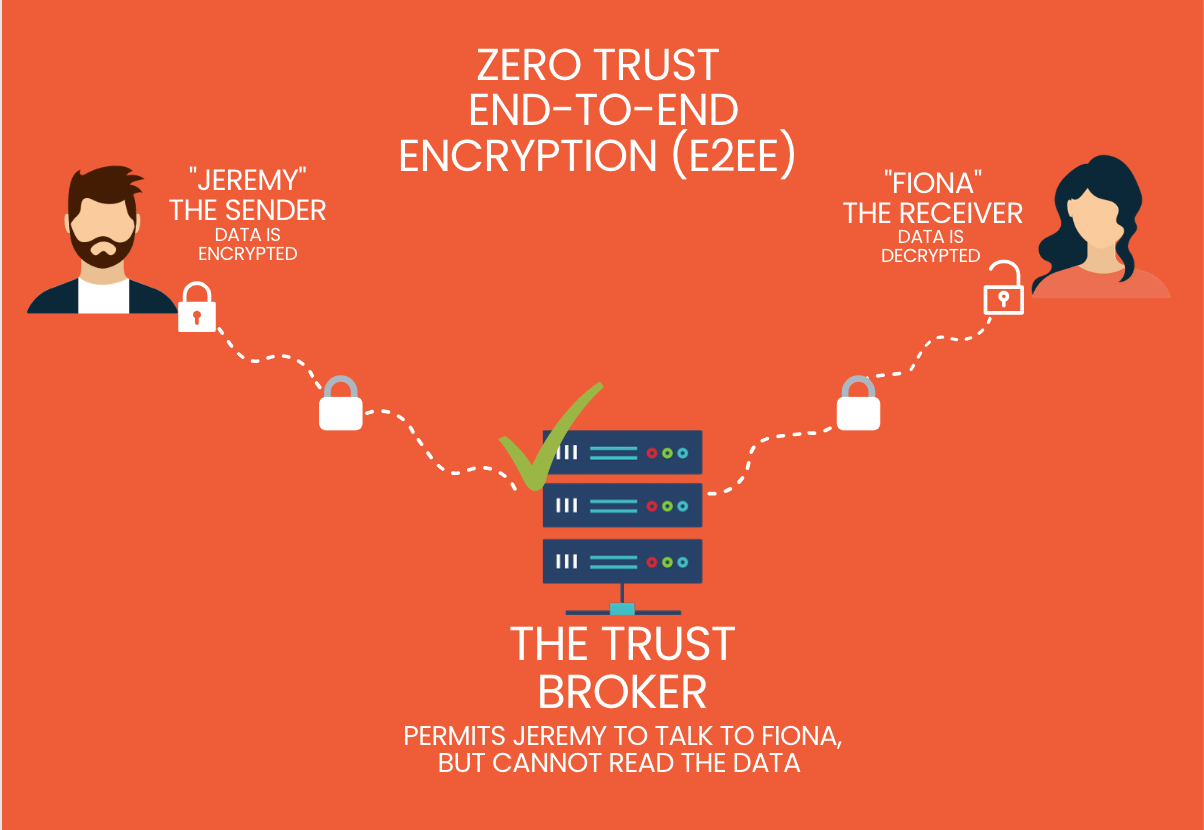
Encryption is a process that involves transforming plain text information into encoded data using algorithms. This encoded data, known as ciphertext, appears as a meaningless string of characters to unauthorized individuals. Only authorized parties in possession of the proper encryption key can decrypt the ciphertext and regain access to the original information. This ensures that even if the data is intercepted or stolen, it remains useless to anyone without the encryption key.
The Role of Encryption in Blur.io Security
Blur.io understands the significance of maintaining security and confidentiality for its users. Encryption is a fundamental aspect of the platform's security framework. By encrypting sensitive user information, such as login credentials and transaction details, Blur.io ensures that even in the event of a security breach, the data remains secure and protected from unauthorized access. This level of encryption ensures the confidentiality of user data and provides peace of mind to users in their interactions within the blur io platform.
Data Protection
Prevention of Unauthorized Access
Compliance with Privacy Regulations
By implementing robust encryption mechanisms, Blur.io makes a significant contribution to maintaining security and confidentiality on the platform. Users can trust that their personal information and interactions are protected, making Blur.io a reliable and secure environment for their digital activities.
Protecting User Data through Encryption
Encryption plays a crucial role in maintaining the security and privacy of user data in any online platform, including Blur.io. By employing advanced encryption techniques, Blur.io ensures that user information remains secure and inaccessible to unauthorized individuals.
When users interact with the Blur.io platform, their data, including personal information and transaction details, are encrypted using robust algorithms. This encryption process converts the data into unreadable and scrambled characters, which can only be decrypted using an encryption key.
The use of encryption on Blur.io provides several key benefits:
Data Security: Encryption helps protect user data from unauthorized access, ensuring that sensitive information such as passwords, financial details, and personal identifiers are stored securely.
Privacy Protection: By encrypting user data, Blur.io ensures that personal information remains confidential and safe from any intrusion or exploitation.
Secure Transactions: Encryption plays a crucial role in securing transactions made on the Blur.io platform, preventing any interception or tampering of data during the process.
Compliance with Regulations: By implementing encryption, Blur.io complies with various data protection and privacy regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Overall, encryption is a fundamental aspect of maintaining user data security and privacy on Blur.io. It ensures that data remains confidential, provides a secure environment for transactions, and adheres to regulatory requirements. By implementing robust encryption techniques, Blur.io aims to instill trust and confidence among its users.
For more information on how Blur.io maintains security and the advantages of using the platform, you can Se connecter à Blur.io : Explorer les caractéristiques et les avantages de Blur.io.
Securing Communications with Encryption
Encryption plays a crucial role in maintaining the security of communications on the Blur.io platform. By utilizing encryption technologies, Blur.io ensures that sensitive information shared between users, such as login credentials and transaction details, remains protected from unauthorized access.
When users access the Blur.io platform, their communication with the server is encrypted using advanced encryption algorithms. This means that any data transmitted between the user's device and the server is scrambled, making it unintelligible to any outside party that may intercept it.
The encryption process starts with the user's device generating a unique encryption key, also known as a public key. This key is used to encrypt the data before it leaves the device. Once the encrypted data reaches the server, it is decrypted using a corresponding private key held by the server. This ensures that only the intended recipient can access and understand the information exchanged.
Encrypting communications on the Blur.io platform not only protects against eavesdropping and unauthorized access but also safeguards users' privacy. It prevents third parties from obtaining sensitive information and helps maintain the confidentiality and integrity of all interactions on the platform.
By implementing strong encryption protocols, Blur.io ensures that user data remains secure, enhancing trust and confidence in the platform. This security measure is essential in today's digital landscape, where cyber threats and data breaches are becoming increasingly prevalent.
For users, it is crucial to understand the importance of encryption and its role in maintaining their security on the Blur.io platform. By utilizing encryption, users can confidently engage in various activities on the platform, such as browsing the marketplace, conducting transactions, and interacting with other users, knowing that their data is protected.
To protect your communications and take advantage of the security features offered by Blur.io, se connecter à Blur.io and explore the platform's features and advantages.
Encryption as a Shield Against Cyber Attacks
In the digital age, cyber attacks have become an increasingly prevalent threat to the security and privacy of individuals, organizations, and online platforms. Hackers constantly seek to exploit vulnerabilities in systems and gain unauthorized access to sensitive information. Encryption serves as a vital defense mechanism, protecting data from falling into the wrong hands and ensuring online safety.
What is encryption?
Encryption refers to the process of encoding information in such a way that only authorized parties can access and understand it. Through encryption, data is scrambled using complex algorithms, making it unintelligible to anyone without the proper decryption key. This ensures that even if a cybercriminal intercepts the data, they would not be able to make any sense of it.
How does encryption work?
When data is encrypted, it goes through a mathematical transformation that alters its structure and appearance. The encryption process typically involves two main components: the encryption algorithm and the encryption key. The encryption algorithm determines how the data will be transformed, while the encryption key serves as the digital "lock" that is required to decrypt the data. Only users with the correct encryption key can effectively unlock and access the encrypted information.
The role of encryption in maintaining security on the blur io platform
On the blur io platform, encryption plays a crucial role in ensuring the confidentiality, integrity, and authenticity of user data. All sensitive information, such as login credentials, personal details, and payment data, undergoes strict encryption protocols to prevent unauthorized access. This includes both data at rest, stored on the platform's servers, and data in transit, being transmitted between the platform and users.
Protecting data at rest: While stored on the blur io platform, user data is encrypted using robust algorithms and secure encryption keys. This ensures that even if the platform's servers were compromised, the encrypted data would be meaningless to hackers.
Securing data in transit: Whenever users interact with the blur io platform through their browsers or mobile devices, data is encrypted to prevent eavesdropping and tampering. Secure communication protocols, such as HTTPS, are utilized to establish a secure connection between the user and the platform, encrypting the data as it travels across the internet.
By implementing encryption as a shield against cyber attacks, the blur io platform prioritizes the safety and privacy of its users. It ensures that their sensitive information remains confidential and inaccessible to malicious actors. Encryption serves as an essential tool in maintaining a secure online environment, fostering trust among users and enabling them to confidently interact with the platform.
Encryption to Prevent Data Breaches
In today's digital age, data breaches have become an alarming threat to the security and privacy of individuals and organizations. With the increasing amount of sensitive information being shared and stored online, it is crucial to implement strong encryption measures to protect this data from unauthorized access.
What is encryption?
Encryption is a process of converting plaintext into ciphertext, which can only be deciphered by authorized parties with the use of an encryption key. By scrambling the data in such a way that it is unreadable to anyone without the key, encryption ensures that even if a breach occurs, the stolen information remains useless to attackers.
Importance of encryption on the blur io platform
Blur io recognizes the criticality of data security on its platform. With millions of users relying on the platform to securely store and share their personal and sensitive information, the implementation of robust encryption algorithms is imperative.
Encryption works hand in hand with other security mechanisms to provide a multi-layered defense against data breaches on the blur io platform. When users upload their data, it is encrypted using strong cryptographic algorithms, making it virtually impossible for anyone without the encryption key to access or read the information.
Dual encryption architecture
In order to enhance security, blur io has implemented a dual encryption architecture. This means that the data is encrypted both when it is in transit and when it is at rest. When users upload or download their files, they are transmitted over a secure connection using encryption protocols like SSL/TLS, protecting them from eavesdropping or interception.
Once the files are saved on the blur io servers, they are stored in an encrypted format. This means that even if someone gains unauthorized access to the server, they will only find encrypted data, rendering it useless without the encryption key.
The need for strong encryption algorithms
As technology advances, so do the methods used by attackers to break encryption. That's why it is crucial for blur io to regularly update and use strong encryption algorithms, such as Advanced Encryption Standard (AES), which is widely recognized as secure and reliable.
In conclusion, encryption plays a vital role in preventing data breaches on the blur io platform. By implementing robust encryption algorithms, blur io ensures that user data is secure both during transmission and storage, providing peace of mind to its users and maintaining the confidentiality of sensitive information.
Ensuring the Integrity of Data with Encryption
Encryption plays a crucial role in maintaining the security and integrity of data on the blur io platform. By applying advanced encryption algorithms, we can protect sensitive information from unauthorized access and tampering.
When data is encrypted, it is converted into an unreadable format that can only be decoded with a specific encryption key. This process ensures that even if a hacker intercepts the data, they would be unable to read or understand its contents without the proper key.
One of the key benefits of encryption is its ability to guarantee the integrity of data. By encrypting data, any unauthorized modifications or alterations to the information can be easily detected. This is because encryption algorithms use mathematical functions to generate a unique signature for each piece of encrypted data. If any changes are made to the encrypted data, the signature will not match, indicating tampering.
A common method used to ensure data integrity is the use of checksums. A checksum is a unique value generated from the data using an algorithm. When the data is decrypted, the checksum can be recalculated and compared to the original checksum. If the checksums do not match, it indicates that the data has been modified.
Encryption also plays a crucial role in protecting data during transit. Data is often vulnerable to interception and eavesdropping when transmitted over networks. By encrypting the data before transmission, we can ensure that even if it is intercepted, it remains secure and cannot be understood by unauthorized individuals.
In conclusion, encryption is of utmost importance in ensuring the integrity of data on the blur io platform. It provides confidentiality, data integrity, and protects sensitive information both at rest and in transit. By implementing robust encryption measures, we can maintain a secure environment for our users and their valuable data.
Encryption in Cloud Storage on the blur io Platform
Cloud storage has become an integral part of our digital lives. It allows us to store and access our data from any device and anywhere in the world. However, this convenience comes with concerns about the security and privacy of our information. That's where encryption plays a crucial role.
Encryption is the process of converting plain text into ciphertext, making it unreadable without the appropriate decryption key. When it comes to cloud storage on the blur io platform, encryption is an essential mechanism that ensures the confidentiality and integrity of your data.
When you upload files to blur io, they are encrypted at rest using strong encryption algorithms. This means that even if someone gains unauthorized access to the cloud storage system, they won't be able to access your files without the encryption key.
Additionally, encryption is also applied during data transmission. When you send or retrieve files from blur io, the data is encrypted using secure protocols such as SSL/TLS. This prevents eavesdroppers from intercepting and deciphering your data while it's in transit.
The blur io platform also offers client-side encryption, which means that you can encrypt your files on your own device before uploading them to the cloud. This gives you full control over the encryption process and ensures that only you have access to the decryption key.
It's important to note that while encryption provides a high level of security, it's not a substitute for other security measures. It's crucial to use strong passwords, enable two-factor authentication, and regularly update your devices and software to further enhance the security of your data on the blur io platform.
In conclusion, encryption plays a vital role in ensuring the security and privacy of your data on the blur io platform. By encrypting your files at rest and during transmission, and by using client-side encryption, you can have peace of mind knowing that your information is protected from unauthorized access.
Encryption in Transit on the blur io Platform

Encryption plays a vital role in maintaining security on the blur io platform, especially during the transmission of data. Encryption in transit refers to the process of encoding data before it is sent over the network, ensuring that it remains confidential and secure.
When users access the blur io platform, they expect their data to be protected from prying eyes and unauthorized access. Encryption in transit achieves this by converting sensitive information into an unreadable format, making it difficult for attackers to intercept and exploit the data.
To ensure the integrity and confidentiality of data transmitted on the blur io platform, industry-standard encryption protocols such as HTTPS (Hypertext Transfer Protocol Secure) are utilized. The use of HTTPS ensures that all communication between the user's device and the blur io servers is encrypted and secure.
In addition to HTTPS, blur io also implements other security mechanisms like Transport Layer Security (TLS) to further enhance the encryption in transit. TLS provides an additional layer of protection by authenticating the server and establishing a secure connection between the user and the platform.
Another aspect of encryption in transit on the blur io platform is the use of secure network protocols. These protocols, such as Secure Sockets Layer (SSL) and Datagram Transport Layer Security (DTLS), add another layer of encryption to the data transmission process, ensuring the data remains secure throughout its journey.
By implementing robust encryption in transit, blur io ensures that users' data remains safe and protected from eavesdropping, man-in-the-middle attacks, and other malicious activities. This commitment to security builds trust and confidence among users, making the platform a secure environment for all data transactions.
The Role of Encryption in User Authentication
When it comes to maintaining security on the blur io platform, encryption plays a vital role in ensuring the authenticity of users and protecting their sensitive information. User authentication is a crucial part of the security measures implemented on the platform, and encryption is the key to its success.
Encryption is a process that converts plaintext data into an unreadable format, known as ciphertext, using mathematical algorithms. This process ensures that sensitive information such as passwords and personal data transmitted by users is secure and protected from unauthorized access.
One of the main challenges in user authentication is to ensure that the person attempting to access the platform is indeed the authorized user. Encryption helps solve this challenge by using cryptographic protocols to verify the identity of users. By encrypting the credentials entered by users during the authentication process, it becomes extremely difficult for attackers to intercept and decipher this information.
Furthermore, encryption also plays a crucial role in protecting user data stored on the platform. By encrypting the data at rest, even if an attacker gains unauthorized access to the database, the data will be useless without the encryption key. This adds an extra layer of security and ensures that user information remains confidential.
End-to-End Encryption
End-to-End encryption is an essential aspect of user authentication on the blur io platform. This technique ensures that the communication between the user's device and the platform's servers is encrypted, making it nearly impossible for any third party to intercept and view the data transmission.
The use of strong encryption algorithms, combined with secure key management practices, makes it challenging for attackers to compromise user authentication and gain unauthorized access to the platform.
The importance of Encryption in User Trust
Encryption plays a significant role in building trust between the users and the platform. By implementing robust encryption mechanisms, the platform demonstrates its commitment to protecting user privacy and data security. This, in turn, enhances the users' confidence in the platform's security measures.
Overall, encryption is a critical component of user authentication on the blur io platform. It ensures the authenticity of users, protects sensitive information, and builds trust between the users and the platform. By leveraging encryption technology, the platform can effectively maintain security and provide a secure environment for users to interact and utilize its services.
The Legal Requirements for Encryption on the blur io Platform

As an online platform that prioritizes user privacy and data security, blur io is committed to adhering to legal requirements regarding encryption. Encryption plays a vital role in maintaining the security and integrity of user information, preventing unauthorized access and maintaining user trust. To ensure compliance, blur io adheres to several legal requirements when it comes to encryption.
Compliance with Data Protection Regulations
Blur io operates in accordance with various data protection regulations, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. These regulations mandate the use of encryption to protect the personal data of users. By employing robust encryption measures, blur io ensures that user information remains secure and that personal data are protected from unauthorized disclosure or access.
Industry-Specific Compliance
In addition to general data protection regulations, blur io also complies with industry-specific regulations that apply to certain sectors. For example, the Health Insurance Portability and Accountability Act (HIPAA) in the healthcare industry and the Payment Card Industry Data Security Standard (PCI DSS) in the financial sector require the use of encryption to safeguard sensitive information. Blur io uses encryption algorithms and protocols that meet the specific requirements of these industries, thus ensuring compliance with these regulations.
Constant Monitoring and Updating
Blur io recognizes that legal requirements and encryption standards evolve over time. To stay ahead and ensure compliance, the platform continuously monitors these changes and updates its encryption practices accordingly. This proactive approach allows blur io to maintain the highest level of security and guarantee that encryption methods remain up to date, meeting current legal requirements at all times.
In conclusion, blur io prioritizes user privacy and data security by adhering to legal requirements for encryption. By complying with data protection regulations and industry-specific standards, blur io ensures that user information remains secure and protected. Additionally, the platform makes it a priority to stay updated with evolving encryption requirements, ensuring ongoing compliance and maintaining the utmost security for users.
Future Developments in Encryption Technology
Encryption technology is constantly evolving in order to keep up with the ever-increasing complexity of cyber threats. As the importance of data privacy and security continues to grow, researchers and experts are working on developing new and innovative encryption technologies to ensure the integrity and confidentiality of sensitive information on platforms such as blur io.
1. Quantum-resistant Encryption
One of the most promising future developments in encryption technology is quantum-resistant encryption. With the advent of quantum computers, traditional encryption algorithms that rely on the difficulty of factoring large numbers may become vulnerable. Quantum-resistant encryption aims to develop algorithms that are resistant to attacks from quantum computers, ensuring the long-term security of encrypted data.
Researchers are exploring different approaches, such as lattice-based cryptography and multivariate polynomial cryptography, to achieve quantum-resistant encryption. These techniques rely on mathematical problems that are difficult for both classical and quantum computers to solve, making them ideal for safeguarding sensitive information against future advancements in computing technology.
2. Homomorphic Encryption

Another exciting development in encryption technology is homomorphic encryption. Traditional encryption methods require decrypting the data before performing any operations on it, potentially exposing it to security risks. Homomorphic encryption allows for computations to be performed directly on encrypted data, without the need for decryption. This enables secure processing of sensitive information while maintaining its confidentiality.
Homomorphic encryption has numerous applications, such as secure cloud computing and data analysis. It allows users to outsource data processing tasks to third-party providers without compromising privacy. By leveraging this technology, blur io can offer advanced analytics and computations on encrypted data, ensuring that user information remains secure throughout the data processing pipeline.
3. Post-quantum Cryptography

In addition to quantum-resistant encryption, post-quantum cryptography is another area of ongoing research. Post-quantum cryptography aims to develop encryption algorithms that are secure even against attacks from both classical and quantum computers. This is crucial for ensuring the long-term security of sensitive information in an era where quantum computing is becoming a reality.
Researchers are exploring various cryptographic primitives, such as code-based cryptography, lattice-based cryptography, and hash-based cryptography, to develop secure post-quantum encryption algorithms. By adopting post-quantum cryptography, blur io can strengthen its security measures and protect user data from potential quantum computing threats.
In conclusion, the future of encryption technology looks promising, with ongoing research and development in areas such as quantum-resistant encryption, homomorphic encryption, and post-quantum cryptography. These advancements will play a crucial role in maintaining the security of platforms like blur io, ensuring the confidentiality and integrity of sensitive user information in the face of evolving cyber threats.
What is encryption and how does it help maintain security on the blur io platform?
Encryption is a method of encoding information or data in a way that only authorized parties can access and understand it. On the blur io platform, encryption plays a crucial role in maintaining security by securing the transmission and storage of sensitive user data. It ensures that user information, such as login credentials or personal details, is encrypted before being sent over the internet, making it extremely difficult for hackers or unauthorized individuals to intercept or decipher the data.
Why is encryption important on the blur io platform?
Encryption is vital on the blur io platform to ensure the security and privacy of user data. Without encryption, sensitive information would be vulnerable to interception and misuse by unauthorized entities. By encrypting data, the blur io platform provides an extra layer of protection, making it significantly harder for attackers to gain access to sensitive user information.
How does encryption work on the blur io platform?
When a user interacts with the blur io platform, their data is encrypted using complex algorithms. This process converts the data into an unreadable format, known as ciphertext. Only authorized parties with the correct decryption key can convert the ciphertext back into its original form, known as plaintext. This ensures that sensitive user data remains confidential and secure, even if intercepted by hackers or other malicious entities.
What are the potential risks if encryption is not used on the blur io platform?
If encryption is not used on the blur io platform, sensitive user data would be at risk of unauthorized access, interception, and misuse. Potential risks include data breaches, identity theft, unauthorized transactions, and exposure of personal information. Without encryption, hackers or malicious entities may be able to intercept user data and exploit it for personal gain or to commit fraudulent activities.
Can encryption be bypassed or hacked on the blur io platform?
While encryption on the blur io platform is designed to be highly secure, no encryption method is entirely foolproof. Given enough time, resources, and computing power, it is possible for skilled hackers to bypass or crack encryption algorithms used by the platform. However, implementing robust encryption protocols and regularly updating them significantly reduces the chances of successful hacking attempts. The blur io platform stays proactive in updating its encryption methods to stay ahead of potential threats.
What is encryption and why is it important for security on the blur io platform?
Encryption is the process of encoding information in such a way that only authorized parties can access it. It is important for security on blur io platform because it ensures that sensitive data, such as user passwords and personal information, cannot be easily intercepted or accessed by unauthorized individuals. Encryption protects the privacy and confidentiality of user data and helps to prevent identity theft and unauthorized access to personal accounts.
How does encryption work on the blur io platform?
Encryption on the blur io platform works by using cryptographic algorithms to convert plain text data into encrypted data. This encrypted data can only be decrypted and accessed using a specific encryption key, which is known only to the authorized parties. The encryption process ensures that even if the encrypted data is intercepted, it cannot be deciphered or understood without the encryption key. This adds an additional layer of security and helps to maintain the confidentiality and integrity of user data on the blur io platform.
What are the potential risks of not using encryption on the blur io platform?
The potential risks of not using encryption on the blur io platform are significant. Without encryption, sensitive user data, such as passwords, credit card information, and personal details, can be easily intercepted by hackers or malicious individuals. This can lead to identity theft, unauthorized access to personal accounts, and financial loss. Additionally, without encryption, there is a higher risk of data breaches and data leaks, as unauthorized individuals can easily access and exploit unencrypted data. Encryption is essential for maintaining the security and integrity of user data on the blur io platform and protecting users from potential risks and vulnerabilities.
Blur: NFT | Blur: NFT login | Blur: NFT connect | WalletConnect | Traders | What Is Blur Crypto
2022-2024 @ The importance of encryption in maintaining security on the blur io platform